6 Things That Happen When You Respond To A Phishing Email

Have you ever been told, “Don’t feed the trolls”? This piece of advice is golden in online forums and social media, advising us not to engage with those seeking to provoke. Similarly, in the world of cybersecurity, there's an equivalent saying that is every bit as prudent: “Don’t respond to phishing emails!”
It’s easy to underestimate the danger, with many people viewing phishing emails as more of an annoyance than a genuine threat. Yet, even a single response, perhaps driven by curiosity or annoyance, can open Pandora’s box of cyber trouble.
In this blog post, we will uncover what happens if you respond to a phishing email.
Jump To What To Do If You've Responded To a Phishing EmailWhat You'll Learn In This Article.
- How responding to a phishing email signals to attackers that they've reached an active account.
- The effects that conversing with an attacker has on your email security tools.
- What an attacker can do with your information.
- The risk of attackers exploiting human nature to build rapport through regular communication.
- Why the attack might not be immediate after responding to a phishing email.
- The steps you should take if you suspect you've responded to a phishing email.
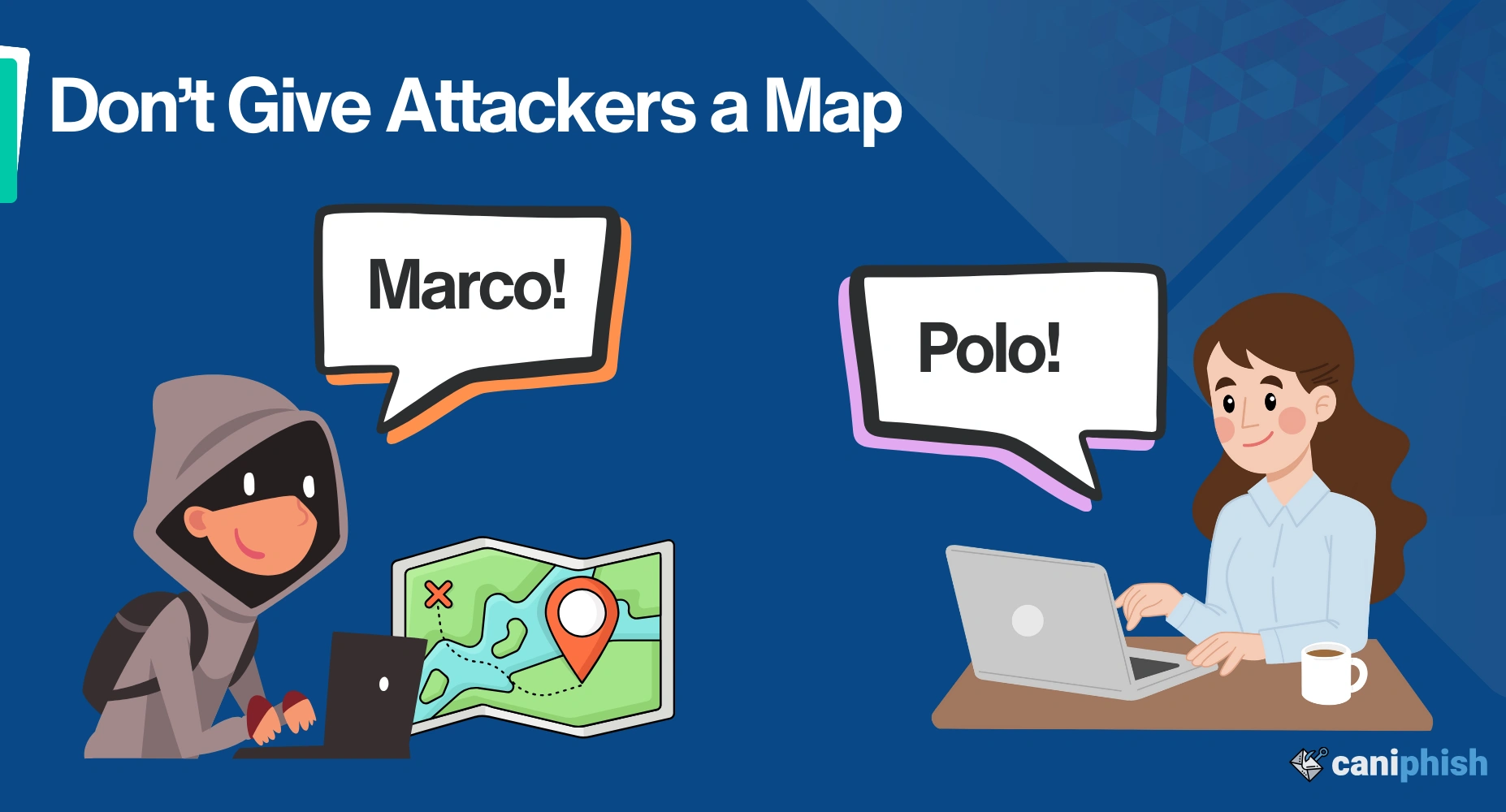
1. You’re Telling Attackers Where to Attack
By responding to a phishing email, you're basically waving a big bright flag, saying, “Hey! This is an active email account!” For cybercriminals, this knowledge is valuable. Why? Because it confirms that your email address is valid and frequently monitored.
If you respond to a phishing email, you're essentially playing a digital version of "Marco Polo" with the attacker. When the email is sent to you, the attacker is yelling "Marco!", your response is the equivalent of you shouting "Polo!" loudly and clearly, signaling that you’re present, engaged, and ready for them to hone in on!
2. You’re Misleading Your Email Security Tools
Just like us, our email security tools learn from patterns. A continued back-and-forth conversation with a phishing email might lead your email security tools to assume the sender is genuine.
This technology is cleverly designed not to impede our daily conversations and activity. It learns who to trust by monitoring who you communicate with. It's a feature, not a bug.
The result? Your email security tools may inadvertently prioritize emails from that suspicious sender in the future—even when they contain more sinister content!
Let’s look at a realistic scenario to see how responding to a phishing email can play out.
When Trusty Tools Are Tricked
Imagine you’re the sales manager at a tech firm. One day, you receive an email from "FutureTech" discussing the latest tech trends. Though slightly puzzled, you assume it’s your sales manager counterpart from one of the many companies you spoke with at a recent conference.
You engage in a back-and-forth conversation about emerging technology in your field. Your email security tools, noting the interaction, mark FutureTech as a trusted contact.
Weeks later, you receive another email from FutureTech. This time, it’s a presentation, a promised glimpse into groundbreaking innovations! Your security algorithms see no threat and give the green light.
Wary, you consider if you should open the unexpected email, but trusting your security tools and are driven by curiosity and the prospect of new knowledge, you open the file. Uh-oh! Instead of slides, nothing appears to happen.
Unbeknownst to you, this file is not what it seems; malware quickly infiltrates your company’s network.
This scenario underscores the dual-edged nature of adaptive email security — its learning capability can sometimes be misled, turning a feature into a potential vulnerability.

3. You’re Unwittingly Handing Out Your Info
Many believe their email signature—typically containing their name, job title, phone number, and sometimes even a physical address—is harmless. After all, this is just the basic 'get-to-know-me' info you'd share at a networking event, isn’t it?
In the wrong hands, this kind of information can be used against you. Here’s how attackers could leverage the data from your email signature:
-
Impersonation: Knowing your full name and job title, cybercriminals can impersonate you, especially in a fast-paced organisation where one doesn’t have time to scrutinize every email.
Picture this: an email, apparently sent by you, lands in your colleague’s inbox, urgently seeking confidential files. Considering its source, why would they hesitate?
-
Reconnaissance for Spear Phishing: With specifics like your direct number or your role in the company, attackers can tailor their approach to be much more believable.
For example, if they know you’re the “Chief Information Security Officer”, they wouldn’t waste their time with the trusty ol’ “You’ve won 1 million dollars email for the net noobs”. They might craft a more targeted message related to software updates or a security breach.
-
Using Your Location: By knowing where you are, an attacker can craft more convincing phishing messages based on your locality, using familiar businesses, events, or news. This technique is refered to as contextual phishing.
To illustrate how an attacker could take advantage of the information provided in your email signature, let's play out a real-world scenario that starts in your office on a regular day and ends in disaster.
A Cautionary Tale of Clicks and Consequences
The aroma of freshly brewed coffee fills the air as you settle into your desk, the hum of the air conditioning and the clatter of keyboards creating a familiar symphony of another day at the office. Your computer springs to life, the usual barrage of unread emails awaiting your attention. You sift through the usual updates, newsletters, and reminders when suddenly, an unusual alert breaks the monotony!
“Police Investigation: Immediate Action Required”, the subject reads. It’s an email from the local police department directly addressed to you. A surge of adrenaline rushes through your veins. Your heart beats faster, and your curiosity is on the brink of overflowing!
A burglary at your office - the message reveals! The lead detective requests your immediate co-operation. Attached is a Word document; they are seeking detailed information to facilitate the ongoing investigation.
As a die-hard follower of true-crime podcasts and detective series, the thrill of being part of a real-life investigation is irresistible. This is not just another day at the office; this is an unexpected twist, an adventure unfolding in real-time! You go ahead and click 'download'.
Thoughts of Sherlock Holmes and Nancy Drew cross your mind as you eagerly wait for the document to spring to life. Little do you know, lurking beneath the surface of that seemingly innocent file is a nasty piece of malware that is currently being installed on your system!
This example shows how easy it can be to be fooled. We naturally trust and want to help, especially when something feels important or when it seems like a person of authority is asking.
In this next example, we'll see how the attacker fine-tunes their approach by using details like the company name, the victim’s job title, and some private info picked up from the response to craft a more customized spear phishing attack. Would you be able to spot this phishing attempt?

4. You’re Unknowingly Building Trust With The Enemy
We all approach unfamiliar emails with a touch of caution. However, we humans are naturally inclined to trust over time.
Building rapport, even with a potential threat, is almost second nature to us. It's how we’re wired. Recognizing this vulnerability is the first step.
Let's look at another real-world example showing rapport built over time and how responding to a phishing email can end in catastrophe.
How Trust Is Built And Exploited Over Time
One day, you receive an unexpected email. The supposed sender introduces themselves as "Jake from the New York Office.” You work for a large tech company that is rapidly growing and establishing offices across the globe. While you've always prided yourself on knowing your colleagues, your company's rapid expansion makes it hard to keep up, so while you didn't expect the email, you don’t think twice about responding to your new friend.
Jake emails you from time to time, mainly to chat about company updates that are in the news. He’s chatty, and despite his appalling grammar, his messages offer a brief respite from the daily slog, you welcome the distraction.
Then, one day, your pal Jake asks you for a quick favor: he's having some tech issues and asks you to confirm your login details. Trusting Jake, you quickly oblige, believing you're just helping out.
Jake, who is actually a seasoned cybercriminal, uses your credentials to access sensitive financial documents about the upcoming merger and lands you and your company in serious hot water!
This fictional, but highly plausible story showcases how cybercriminals can be patient, grooming their targets for weeks or even months! This slow-burn approach ensures that when they strike, you’re less likely to see it coming.
5. You’re Entering the Attacker’s Long-Term Radar
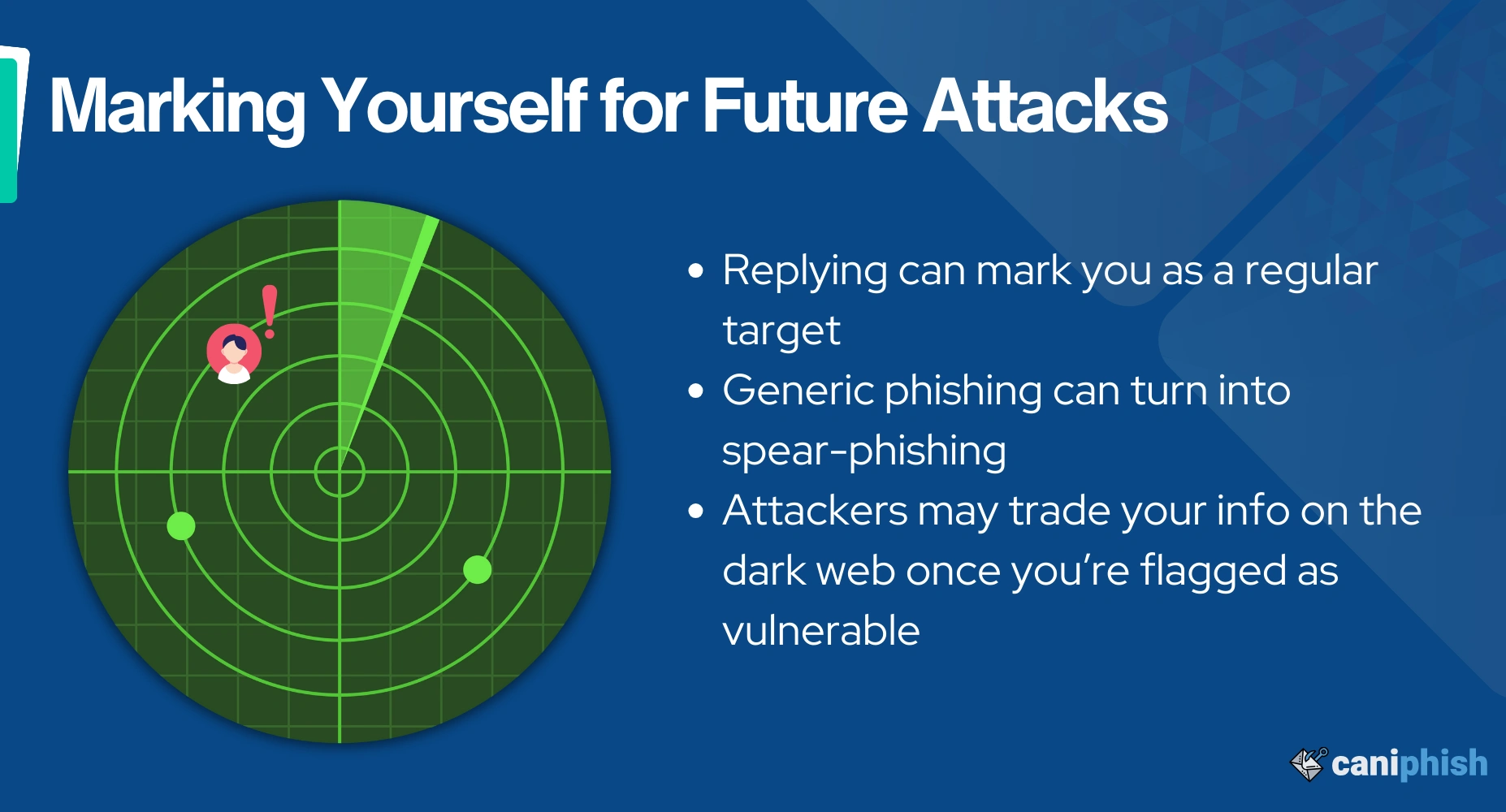
You clicked reply on that suspicious email, thinking, "What's the worst that could happen? If they respond, I'll just hit delete." While this line of defense has its merits, there's a catch: the actual attack might come further down the track when your guard is down.
With your response, you could inadvertently become a ‘regular’ on their hit list. What starts as generic phishing can gradually morph into intricate spear-phishing schemes tailored just for you. As they gather more intel, their approach becomes more genuine and, consequently, more dangerous.
The more they know, the more convincing and dangerous their tactics become!
But the story doesn't end with that lone attacker. Once marked as 'responsive' or 'vulnerable', your details might be traded in the dark corners of the web, exposing you to further risks.
6. You’re Feeding AI‑Driven Phishing Engines
Phishing today isn’t just about tricking one person with a personalized email. Massive campaigns are pulled off using AI. Your response is fuel for the engine.
When you reply, every element of your message becomes data: your tone, phrasing, signature, even your job title or writing quirks. That information may be fed into AI models that craft ultra‑personalized spear phishing. What attackers do with that data:
- Fine‑tune future messages so they feel less robotic and more “someone you know”
- Clone your style to impersonate you
- Build huge datasets so they can scale up attacks with automation.
In short, replying doesn’t just tell them you’re active. It teaches the attacker’s AI how to phish better. And not just against you, but everyone on their list.
You become training data.

You’ve Responded to a Phishing Email. What Now?
Realizing you've responded to a phishing email can be alarming, but taking swift action can significantly minimize potential damage. The steps you should take depend on the nature and extent of the information you've divulged. Here’s a practical guide on what to do next:
-
Change your passwords: If you've sent someone your login credentials, this is your number one priority. Change the passwords for any accounts you suspect might be compromised, starting with your email account! If financial information was shared, get in touch with your bank immediately and follow their advice.
Top tip: Check out our blog post '10 Tips To Create A Strong Password' and learn how to create easy-to-remember passwords that would take centuries to crack.
- Enable multi-factor authentication: Strengthen your defense by implementing multi-factor authentication. This added layer of security ensures that unauthorized users can't access your accounts, even if they have your password.
- Scan for malware: Use a reliable antivirus program to scan your system for malware or viruses.
- Report the phishing email: Alert your email provider about the phishing attempt. If the incident occurred at your workplace, notify your IT department immediately. Remember, if you’ve been targeted, others in your network might be at risk too.
-
Educate yourself and others: As Benjamin Franklin famously said, "An ounce of prevention is worth a pound of cure," rings particularly true in cybersecurity. Consider enhancing your knowledge through security awareness training.
Top tip: Use our free resources and share this blog with friends, family, and colleagues to help them avoid phishing scams.
Deepfakes are no longer science fiction
Watch a free training video and and learn all about deepfake awareness!
Frequently Asked Questions
Can you get hacked by replying to an email?
Yes, you can get hacked by replying to an email, especially a phishing email. In most cases, it's not the response that causes the breach but the subsequent actions that follow. When you respond, you confirm that your email account is active, making you a target for further attacks. Your email security tools might then recognize the attacker as someone you trust, allowing future phishing attempts to land directly in your inbox. Additionally, any personal information you provide can be used for hard-to-spot spear-phishing attacks against you.
What are the consequences of falling for a phishing email?
Falling for a phishing email can have serious consequences. Your credentials may be compromised, allowing attackers to access your accounts. You might inadvertently install malware, leading to data theft or system damage. Sharing banking details on a fake phishing website can result in unauthorized transactions and financial loss. In a business setting, such an attack could cause a data breach, exposing sensitive information and damaging the organization's reputation.
Should I respond to a suspicious email?
No, you should not. If you notice any red flags, you should exercise extreme caution and follow best practice cybersecurity advice. Do not click on any links, open attachments, or reply to suspicious emails. Instead, verify the sender through trusted means, such as contacting them directly using a known, legitimate phone number or email address. If a suspicious email occurs at work, immediately report it to your email provider or IT department.
What happens if I open a phishing email?
Nothing bad will happen from simply opening or viewing a phishing email. In fact, thoroughly viewing emails is one of the best ways to determine if an email is legitimate or malicious. However, remain careful not to perform any action, such as downloading an attachment, clicking a link, or responding. Additionally, be careful not to enable the downloading of images embedded within the email, as this can expose information such as your IP address to the email sender.
How can Generative AI be used to automate and personalize phishing attacks?
Generative AI automates phishing attacks by engaging victims in conversations. The information revealed during these conversations is then used to craft a personalized phishing payload uniquely targeted to the victim and context of the conversation. These attacks can be fully automated, highly personalized, and done on a large scale.
Gareth Shelwell
An Ops Manager dedicated to helping you safely swim amongst the internet of phish!