Free Phishing Websites
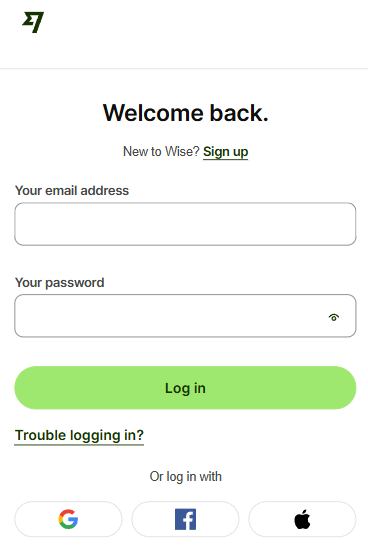
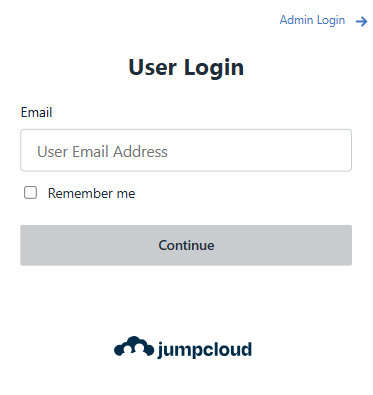
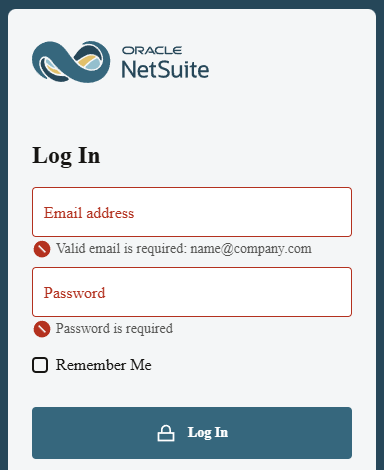
CanIPhish maintains an ever-evolving library of free phishing websites that update with the latest trends. Don't just take our word for it. Take a look at some of the websites in our library!
How Are Phishing Websites Used?
Cybercriminals typically combine phishing websites with phishing messages to lure victims. Phishing messages are typically personalized and paired directly with a relevant phishing website. The websites themselves can either be a single phishing page or a complete copy masquerading as a legitimate website. The type of phishing website created will vary depending on the cybercriminal's goal and the defensive controls in place, which may hinder them from meeting this goal.
Phishing Website Library
Now that we know how phishing websites are used, let's take a look at the library of free phishing websites offered by CanIPhish!
Generating Your Own Phishing Links, Websites, and Pages
Are you looking for more information on how attackers create enticing phishing links, phishing pages, or full-blown phishing websites? These topics are shrouded in mystery, but the team at CanIPhish has performed exhaustive research to provide you with the answers you need.
Generating Phishing Links
When creating or generating phishing links, two complications need to be overcome.
Firstly, we need to ensure that phishing links look attractive to potential victims. To do this, we need to ensure there is some level of personalization. We want to ensure that the beginning of the link contains something familiar, perhaps a sub-domain that directly references the service or website being masqueraded.
Secondly, we need to ensure the phishing link doesn't get blocked by popular browser-based protection tools such as Google Safe Browsing, Microsoft SmartScreen, and much more. If a victim can't see the intended phishing page, then it's of no use. Phishing links need to use various evasion techniques such as randomisation, single-use detonation, and much more to evade browser-based protections.
To learn more about the importance of phishing links and how you can get started, see our blog, which details what a phishing link is. Alternatively, if you're curious how QR codes are abused to send phishing links, see our blog which outlines what quishing is.
Generating Phishing Pages
One of the first questions you should ask yourself when creating a phishing website is whether you need to duplicate the entire website or if you only need to make a single phishing page.
This requirement is defined by the type of phishing attack you're performing and what the end goal is. If you just want to harvest user credentials, then a single webpage masquerading as the login page will meet your needs. If you're looking to duplicate the end-to-end workflow of a banking transaction, then perhaps you need to create a complete duplicate of the website.
At CanIPhish, we focus on only creating single phishing pages. We've found that creating complete duplicates of a website can be troublesome and nearly impossible to maintain. Should a provider make a single change to a web API, redesign a page, or make one of a thousand different types of changes, your full copy will be out-of-date and potentially ineffective.
Frequently Asked Questions
What Is A Phishing Website?
A phishing website is a deceptive website designed to masquerade as the website of a trusted organization. These websites are typically operated by cybercriminals with the goal of stealing or capturing sensitive information from a victim. Cybercriminals will commonly use fake login, product, or checkout pages to meet this goal.
Are Phishing Websites Used In Phishing Simulations?
Yes. Using phishing websites in phishing simulations is extremely beneficial for several reasons. Firstly, from a reporting and tracking perspective, it allows organizations to better understand how susceptible an employee is to phishing – did the employee click the simulated phishing link but then close the page after they noticed the suspicious URL? Or did they still proceed to enter their credentials? Secondly, your employees also benefit from seeing the full lifecycle of a phishing attack in action, training them to always look at the URL of any website they visit.