50+ Phishing Email Examples From 2026

- #52 Payoneer Payment Received
- #51 Shared File From Supervisor
- #50 Uber Eats QR Code
- #49 Drata
- #48 HR Peer Feedback Received
- #47 Apple Tax Invoice
- #46 Microsoft Security Alert
- #45 Urgent Software Update Required
- #44 GoDaddy Security Breach
- #43 Email Account Deactivation
- #42 X Content Violation
- #41 Adobe Acrobat Sign Signature Required
- #40 Netflix Password Expiry
- #39 Request For Quote
- #38 Amex Card Confirmation
- #37 Venmo Payment Notification
- #36 TikTok New Device
- #35 Google Workspace QR Code
- #34 Sharepoint Access Request
- #33 Stripe Password Update
- #32 1Password Password Change
- #31 Xero Statement
- #30 GitHub OAuth App
- #29 Spam Filter Quarantine
- #28 Instagram Verification
- #27 Facebook Verification
- #26 Dropbox Verification
- #25 Zoom Invite
- #24 Udemy Free Credits
- #23 Bamboo HR Employee Benefits
- #22 Salesforce Password Expiry
- #21 Return to Work Survey
- #20 Win An iPhone 15 QR Code
- #19 Lyft Free Rides
- #18 Qantas Frequent Flyer
- #17 Fake Meeting
- #16 Western Union Wire Transfer
- #15 New Years Bonus
- #14 Office Holiday Party
- #13 Job Opportunity
- #12 Bank of America Suspended Account
- #11 DocuSign Signature Request
- #10 Microsoft OneDrive File Share
- #9 Microsoft Teams Missed Message
- #8 Slack Password Reset
- #7 LastPass Suspicious Login
- #6 FedEx Shipment
- #5 HR Policy Violation
- #4 Prezzee Gift
- #3 Gmail Blocked Login
- #2 Jira Notification
- #1 Google Drive File Share
- Wrapping Up
Are you looking for some great examples of phishing emails that can be used to phish and train your employees? The following 50 phishing email examples have been curated based on their popularity and effectiveness at training employees!
Jump To The #1 Most Popular Phishing EmailEach email uses a mixture of obfuscation, personalization, and urgency to entice potential victims into interacting with the payload. The percentage of employees who are compromised by these emails varies between 6% and 54%, with the ability to trick even the most trained IT and cyber security professionals.
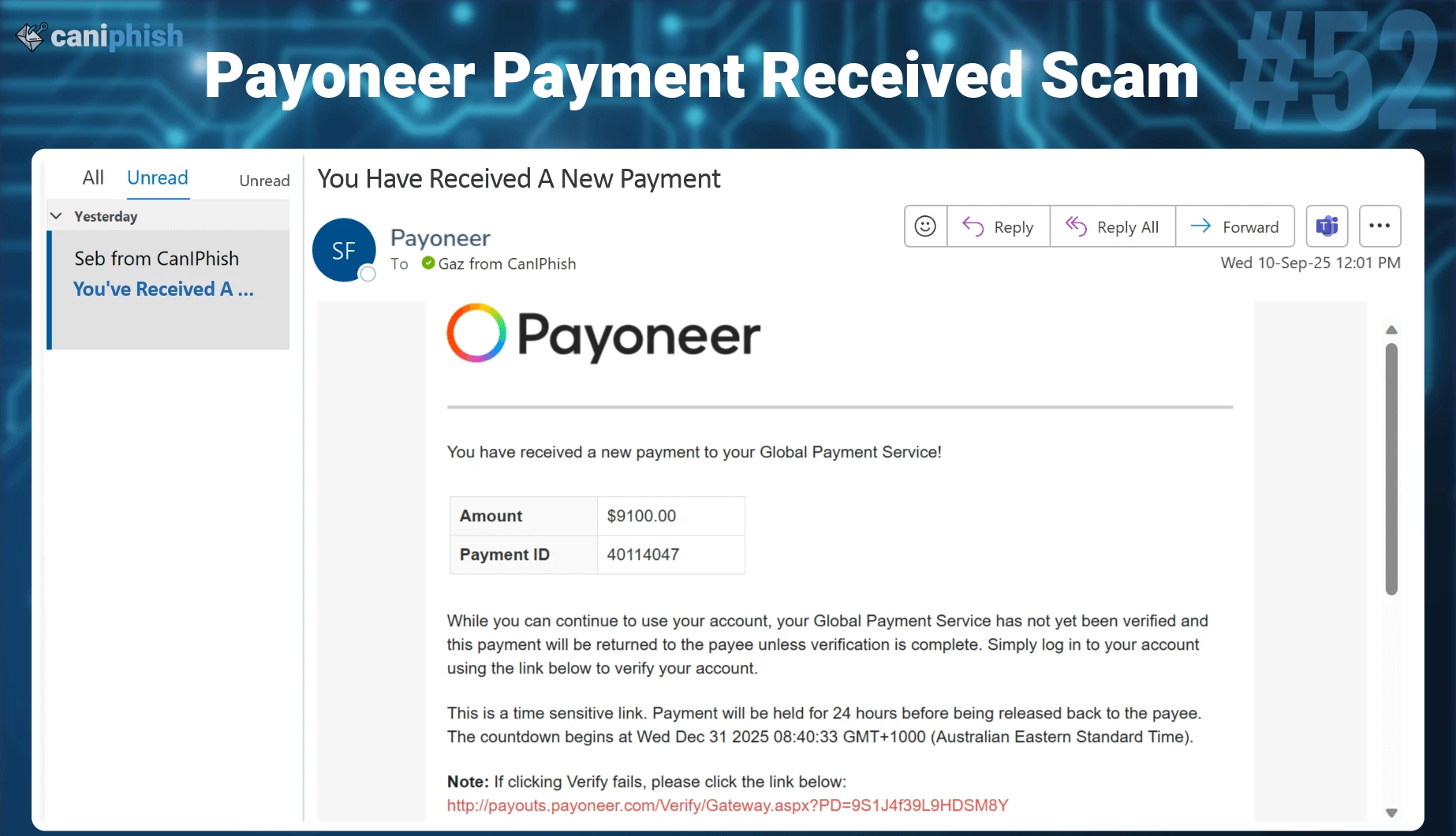
#52 Payoneer Payment Received
Payment notification scams are effective because they trigger curiosity and urgency at the same time. Even users who don’t regularly use a platform may click just to check whether the payment is real or a mistake.
- What is this email? This phishing email claims that a new payment has been received through Payoneer. It displays a big dollar amount, a payment ID, and warns that the funds will be returned unless the account is verified. The message includes a link urging the user to log in immediately to release the payment.
- Why is this email difficult to spot? The email looks like a routine financial notification. It includes realistic payment details and avoids aggressive threats. The urgency comes from the idea of losing money. Many users assume Payoneer notifications are legitimate because the platform is widely used for international payments and contractors.
- Who is prone to falling for this phish? Freelancers, contractors, finance staff, business owners, and anyone who has ever used or heard of Payoneer are at risk. Even users without a Payoneer account may click out of curiosity to check whether someone paid them by mistake.
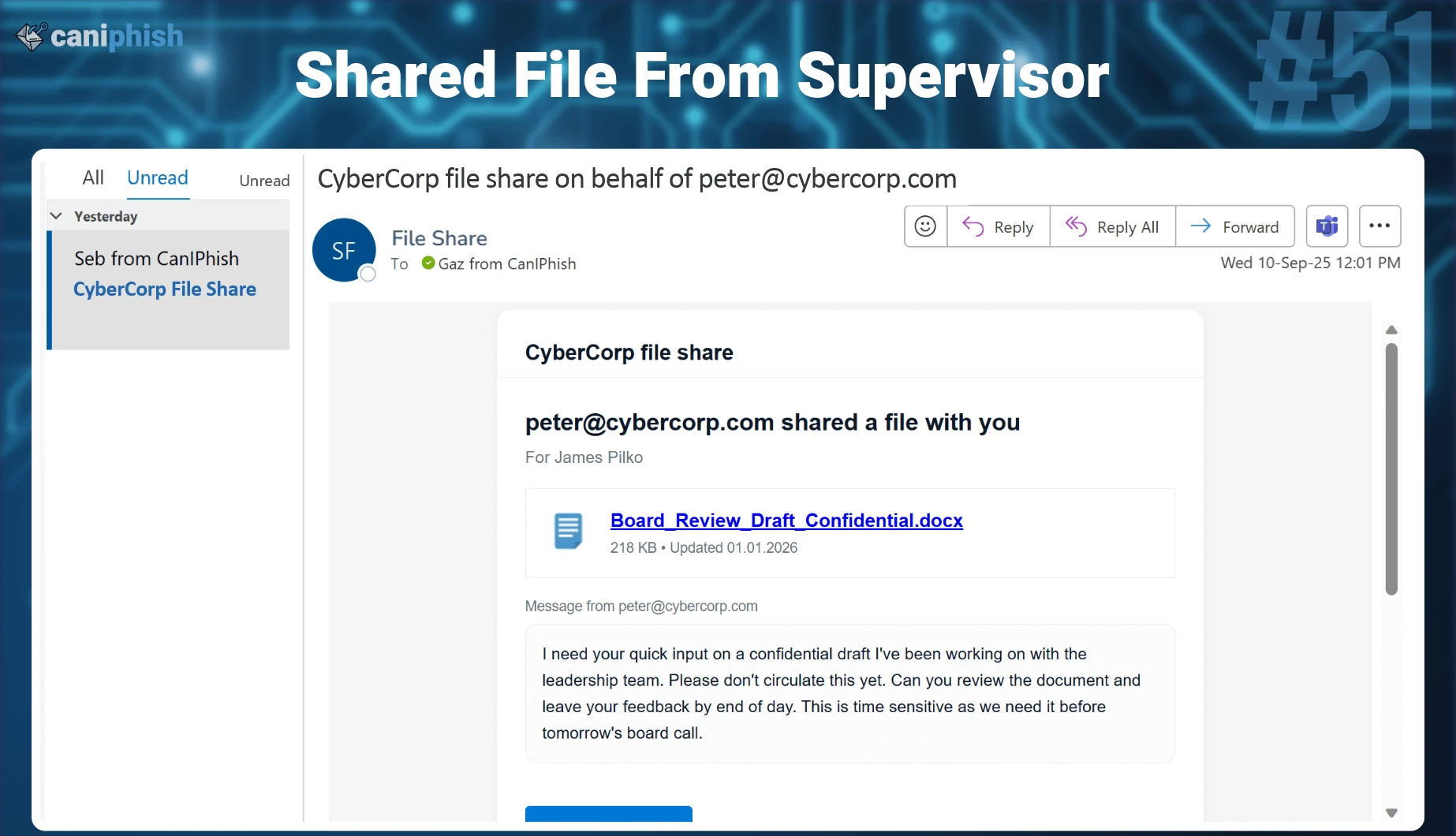
#51 Shared File From Supervisor
File sharing scams work because they blend into everyday business workflows. When it comes from your manager and is accompanied by an added layer of enticement, users are more likely to skip verification and open the file immediately.
- What is this email? This phishing email pretends to be a file sharing notification, claiming that a supervisor has shared a confidential document for urgent review by the end of the day.
- Why is this email difficult to spot? The scenario is very plausible. Managers often share drafts or confidential files for review. The language feels right, not promotional or threatening. The sense of trust comes from the sender relationship rather than branding.
- Who is prone to falling for this phish? This attack targets employees who work closely with leadership, including managers, executives, finance staff, operations teams, and assistants. Anyone used to reviewing internal documents under time pressure is at risk.
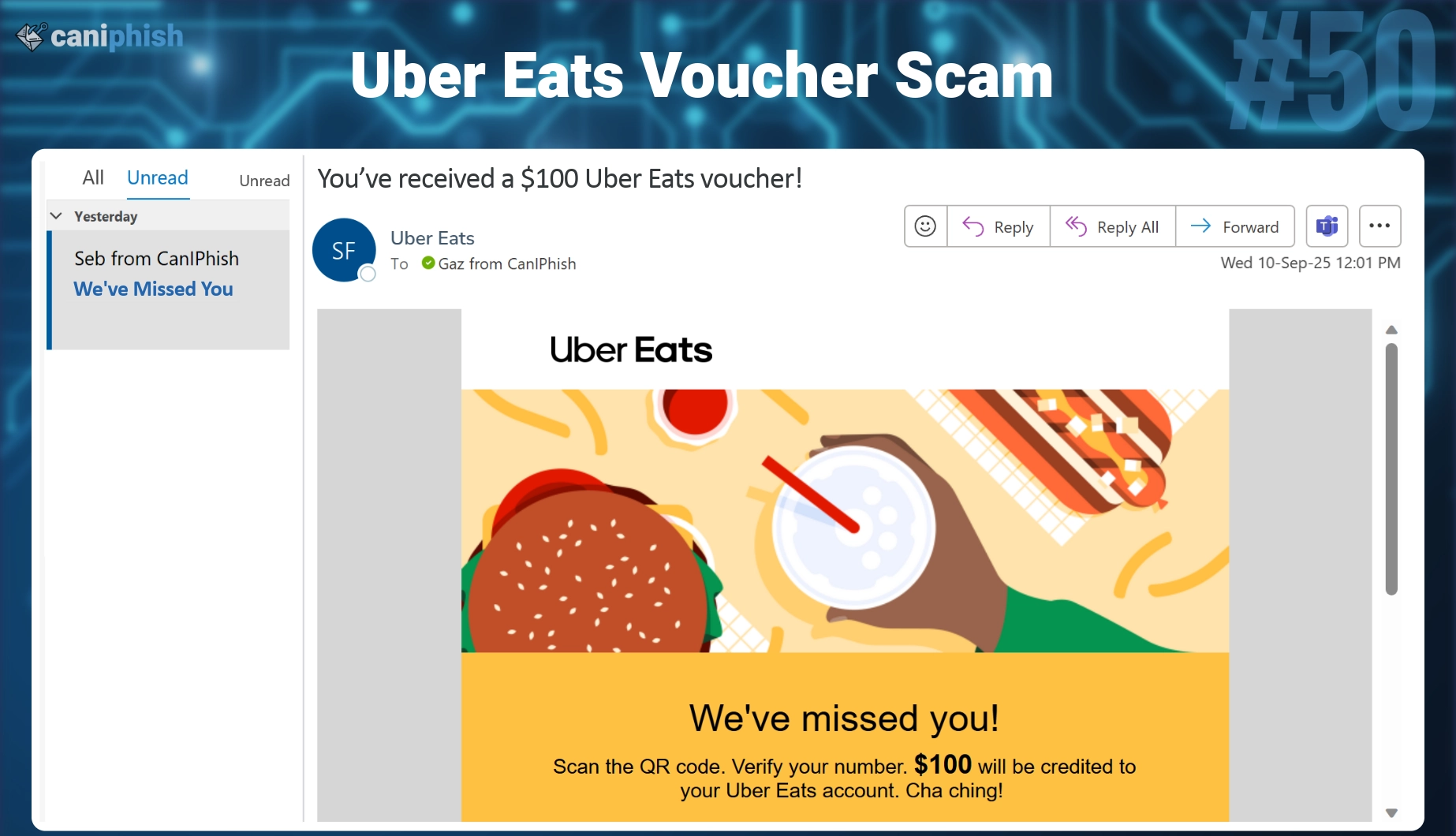
#50 Uber Eats QR Code
Uber Eats is a food delivery platform that connects customers with local restaurants, cafes, and grocery stores through its website and mobile app. Orders are placed and paid for digitally, then delivered to the customer’s location with real-time tracking. Uber Eats is widely used due to its convenience and brand familiarity.
- What is this email? This phishing email claims to be from Uber Eats, saying, “We’ve missed you!”
To win the user back, it offers a $100 voucher redeemable by scanning a QR code. The message includes the scannable image and a promotional offer listed at the bottom. - Why is this email difficult to spot? The offer looks and feels believable. Brands often send loyalty perks or vouchers to re-engage users. The use of a QR code bypasses traditional email link scanning, and many users mistakenly assume QR codes are automatically vetted or safe. Combined with consistent branding, this makes the phish look like a genuine promotion.
- Who is prone to falling for this phish? Anyone who’s previously ordered through Uber Eats, especially casual users or busy professionals. These users are used to receiving promotional offers, vouchers, and marketing emails from the platform, so a $100 voucher offer doesn’t seem unusual.
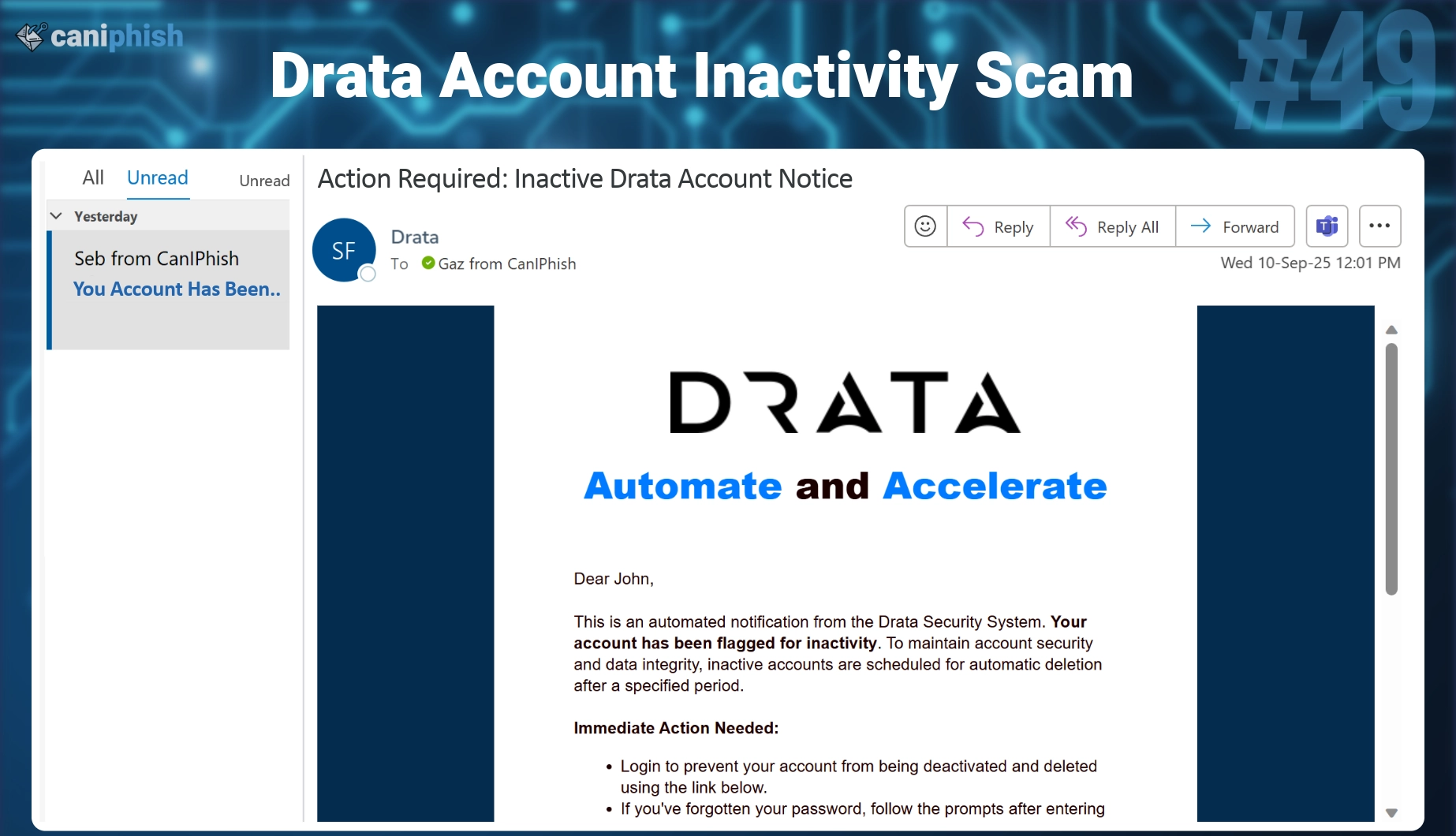
#49 Drata
Drata is a compliance automation platform that helps companies meet security and privacy standards. It connects to a company’s systems and tools to automatically check that security controls are in place and working correctly. By keeping track of these requirements in real time, Drata makes it easier for businesses to stay compliant, prepare for audits, and prove to customers that their data is being handled securely.
- What is this email? This phishing email poses as an automated security notice from Drata, warning the user that their account has been flagged for inactivity and is scheduled for deletion. It urges the recipient to log in immediately using a link in the email to avoid account deactivation and data loss. The message includes call-to-action buttons like “Login to Your Account” and “Recover Your Account.
- Why is this email difficult to spot? It mimics the formal, automated style used in legitimate system alerts because it's brief, technical, and action-focused. The idea of losing access to compliance data or audit tools creates a sense of urgency. The branding is minimal, which actually works in its favor, many real notifications from platforms like Drata are simple by design.
- Who is prone to falling for this phish? This attack targets security professionals, compliance officers, IT admins, legal teams, and anyone responsible for maintaining audit trails or compliance certifications. Users who rely on Drata as part of their daily workflow are more likely to react quickly, without questioning the legitimacy of the request.
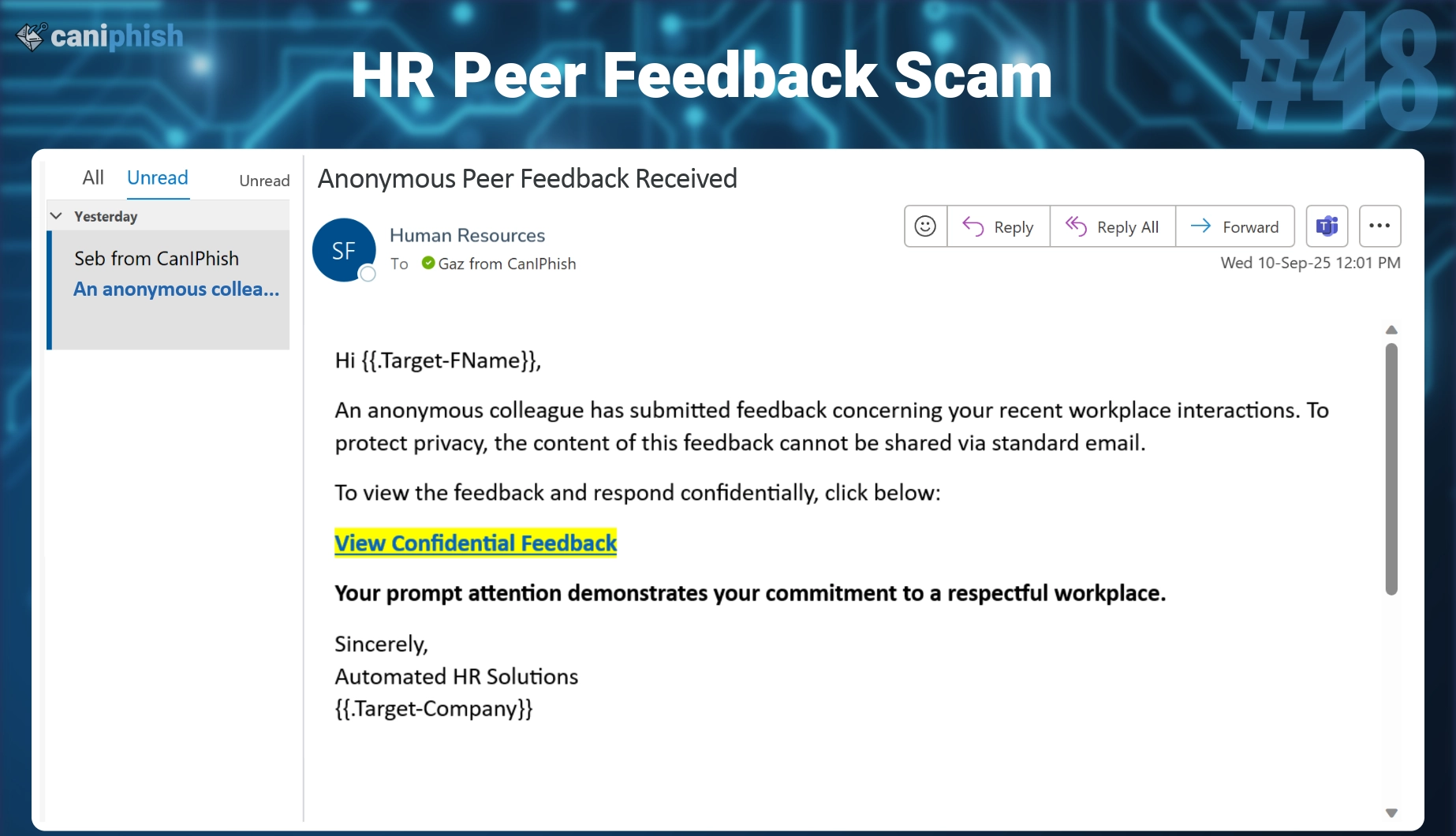
#48 HR Peer Feedback Received
HR-related phishing emails are highly effective because they tap into workplace anxiety and professionalism. Messages about anonymous feedback, complaints, or performance reviews create panic. Victims often click without thinking, just to find out what’s been said about them, especially if the email appears internal, neutral in tone, and uses generic HR branding.
- What is this email? The message attempts to convince recipients that an anonymous colleague has submitted feedback about the recipient's recent workplace interactions. It says the content can't be shared through normal email and urges the user to click a link to view and respond confidentially. The message is signed by “Automated HR Solutions” and references a generic company name to appear internal.
- Why is this email difficult to spot? It avoids obvious red flags by sounding calm, professional, and neutral. The language is vague enough to apply to anyone, yet specific enough to trigger concern. It doesn't rely on fake branding, just a believable scenario. That subtlety makes it harder to detect, especially in companies that use HR portals or anonymous feedback tools.
- Who is prone to falling for this phish? Employees at all levels, especially in large organizations with HR software, peer feedback systems, or performance review cycles, can be at risk. People managers, team leads, and new hires are particularly likely to fall for this type of phish, as they may act quickly to avoid reputational damage.
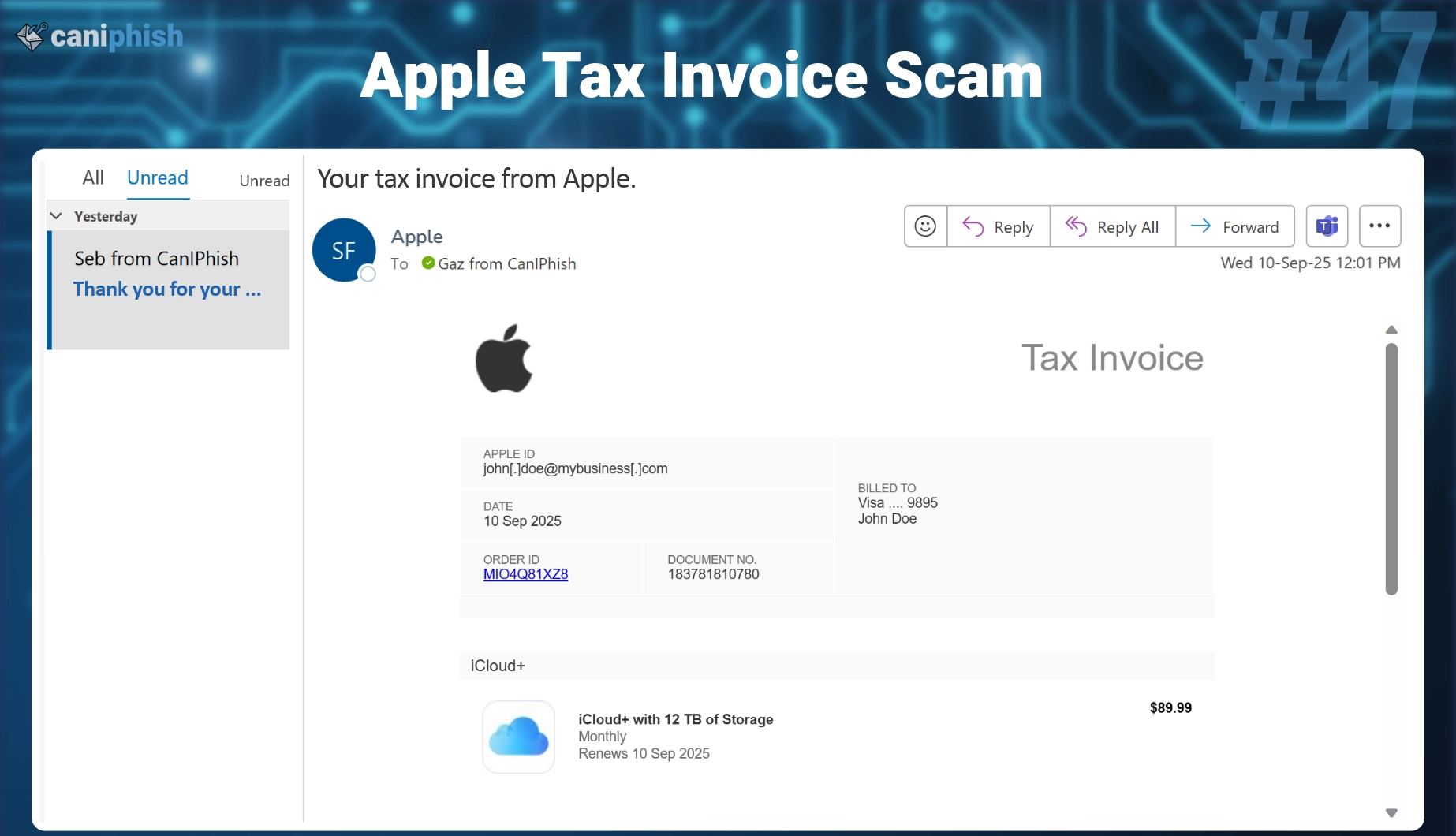
#47 Apple Tax Invoice
Apple is a global technology company best known for products like the iPhone, Mac, iPad, and Apple Watch. It also offers digital services including iCloud, Apple Music, and the App Store. Apple is widely trusted, making it a common target for phishing scams using fake invoices, support alerts, and subscription notices.
- What is this email? It pretends to notify the user of an invoice from Apple, claiming they were charged $89.99 for iCloud + storage. The message includes fake billing details and urges the user to click a link to dispute or cancel the charge. Its simple layout, with an order ID, document number, and masked card details, makes it look believable.
- Why is this email difficult to spot? The layout closely mirrors a real Apple invoice with logos, billing info, and support language. It doesn’t rely on threats, just a confusing charge the recipient wasn’t expecting. The message appears routine, but the pressure to act quickly makes users more likely to click before thinking.
- Who is prone to falling for this phish? Anyone with an Apple ID, especially users who store payment info or manage subscriptions. Busy professionals, parents, or finance staff may skim the email and click instinctively, thinking it's a billing error they need to fix immediately.
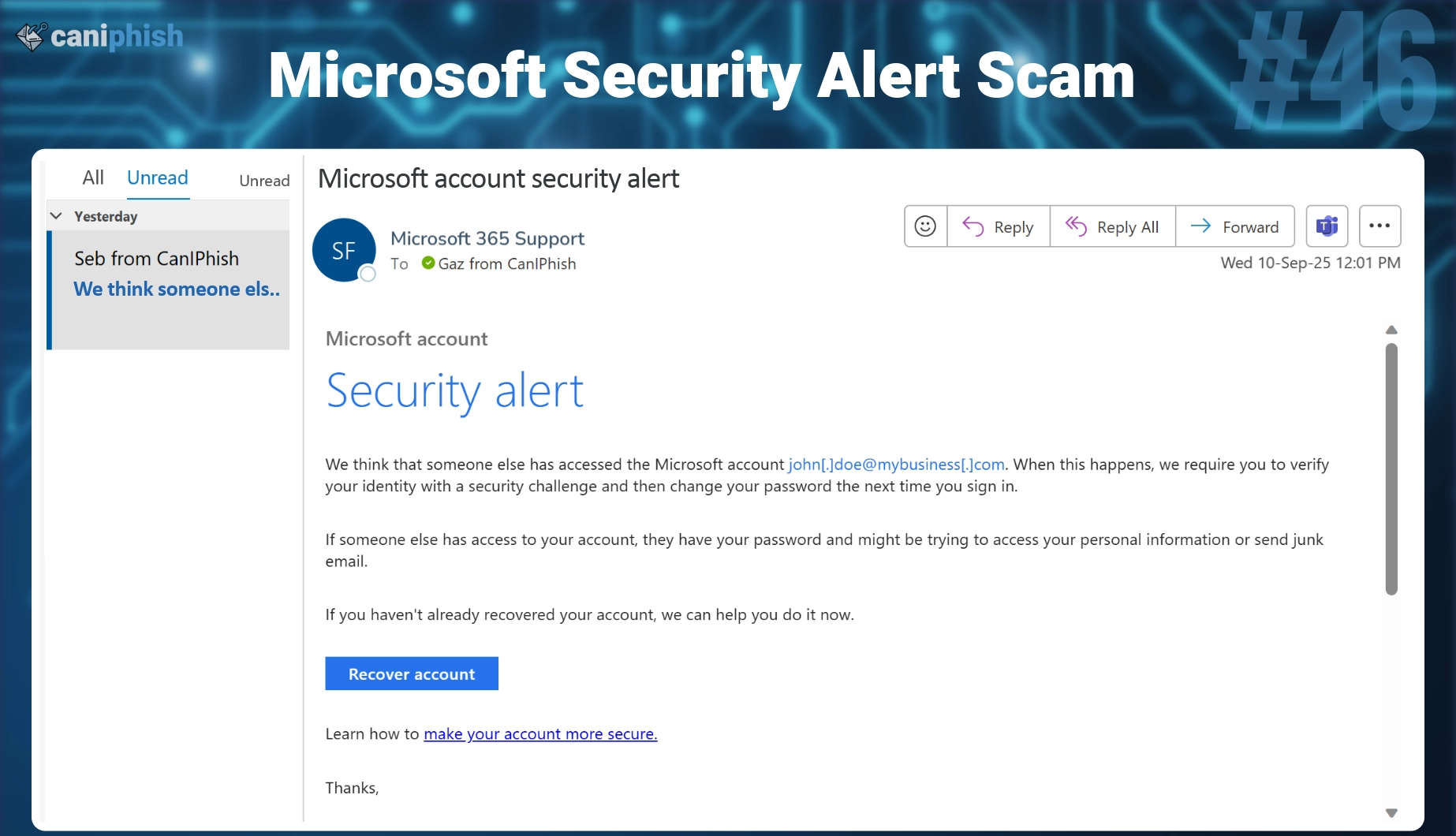
#46 Microsoft Security Alert
Security alerts are among the most convicting email lures. They rely on the fear factor that someone has accessed your account, forcing a quick emotional response to click. Microsoft, being a widely trusted and frequently used platform, is a prime target for these impersonation attacks.
- What is this email? This phishing email pretends to be a security alert from Microsoft, warning the user that someone may have accessed their account. It prompts the user to verify their identity and change their password immediately, providing a “Recover account” button.
- Why is this email difficult to spot? It looks exactly like the real thing, same layout, tone, and footer. Security alerts are common, and the language in this phish is nearly identical to actual Microsoft notifications. The sense of urgency, combined with the fear of account compromise, makes users more likely to act without verifying.
- Who is prone to falling for this phish? Anyone with a Microsoft account, especially employees using Microsoft 365 for work email, files, and Teams. IT staff, admins, and remote workers are particularly at risk, as they often deal with account security and may respond quickly to avoid disruption.
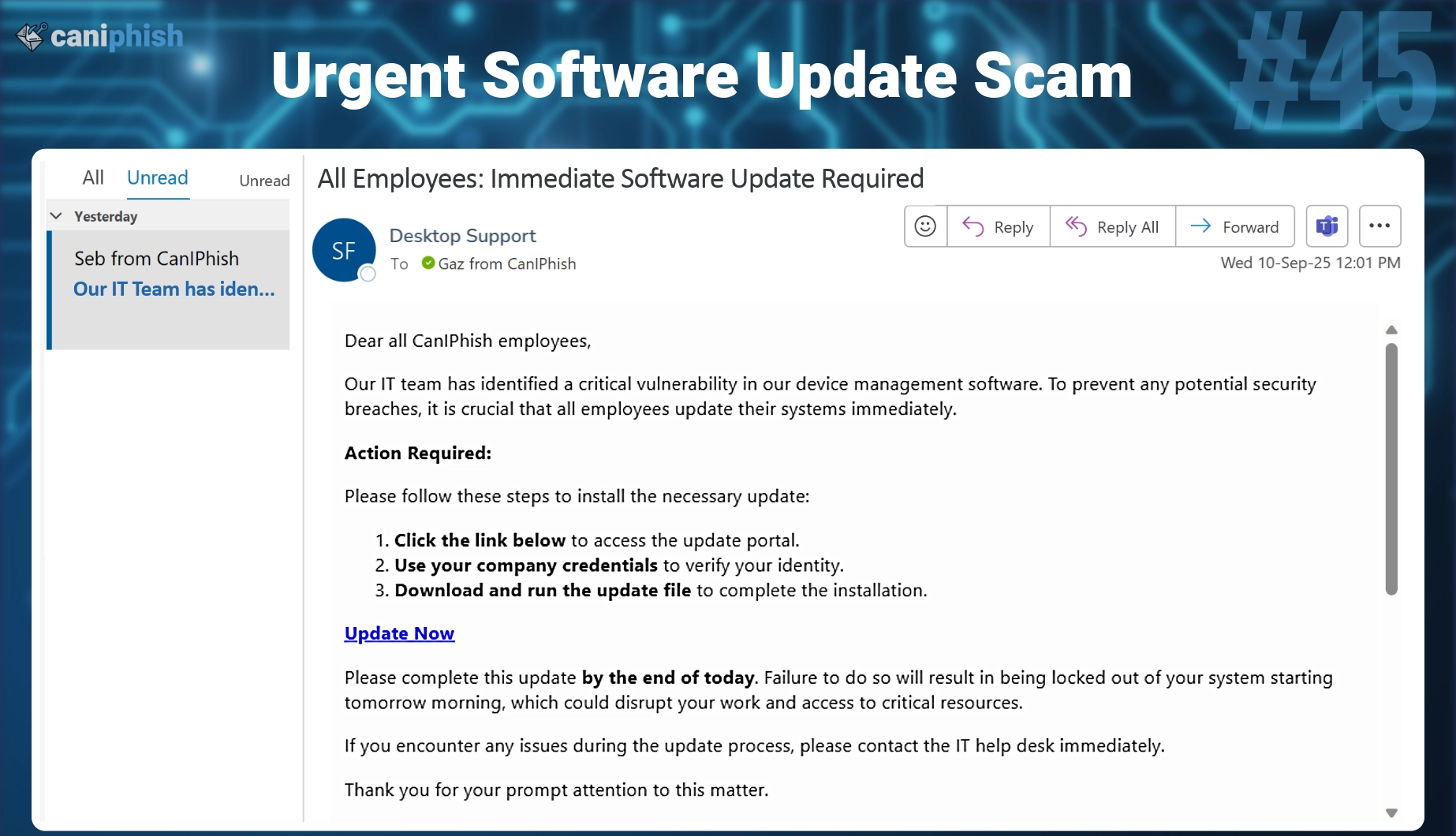
#45 Urgent Software Update Required
Internal IT-themed phishing emails are highly effective because they come across as routine maintenance or urgent security procedures. These emails often impersonate help desk teams and use familiar workflows, like installing software or device updates.
- What is this email? Attackers crafted this email to look like someone from the IT team and claims a critical vulnerability has been found in the device management software. It instructs employees to update their systems immediately and provides a link to an "update portal," where users are told to verify their identity. The message threatens that failure to update will result in being locked out of your system by tomorrow.
- Why is this email difficult to spot? It looks like a standard IT notice with it's formal tone, action steps, and clear deadlines. The threat of being locked out adds pressure to comply immediately. The instructions sound familiar, making it easy to assume it’s just part of standard internal policy. That familiarity lowers suspicion.
- Who is prone to falling for this phish? This targets all employees. These kinds of emails blend in with regular company comms, especially in large organizations. New hires, remote workers, or anyone not closely tied to the IT team are particularly at risk. The combination of urgency and compliance pressure makes this a dangerous and believable phish.
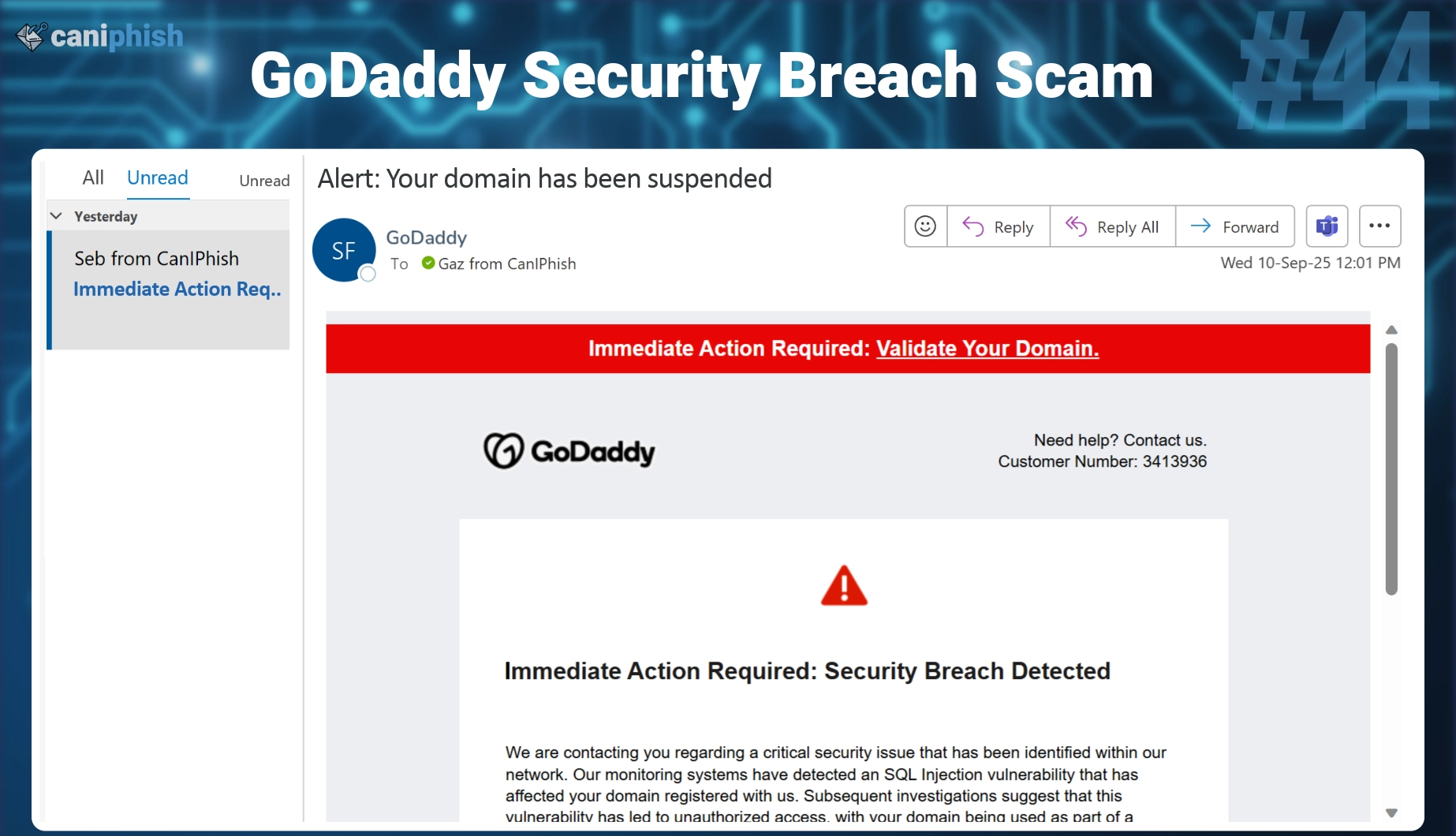
#44 GoDaddy Security Breach
GoDaddy is a domain registrar and web hosting provider. It helps individuals and businesses register website domains, host websites, and manage email and DNS services. With millions of customers worldwide, GoDaddy is a common target for phishing scams involving fake domain renewals, account login alerts, or payment issues.
- What is this email? This phishing email pretends to be a security alert from GoDaddy, claiming that your domain has been compromised. It encourages you to click on the link to validate your domain. Once this is done, they'll restore your domain as soon as possible.
- Why is this email difficult to spot? The email is confronting right away, with a red warning banner and alert icon grabbing your attention. It uses technical terms like “SQL Injection” and “botnet” to sound credible and serious. Phrases like “critical issue” and “illegal activity” ramp up fear and urgency, pushing recipients to act before thinking clearly.
- Who is prone to falling for this phish? Anyone who manages domains, especially small business owners, IT admins, or web developers. People who rely on GoDaddy for hosting or domain services are more likely to take it seriously.
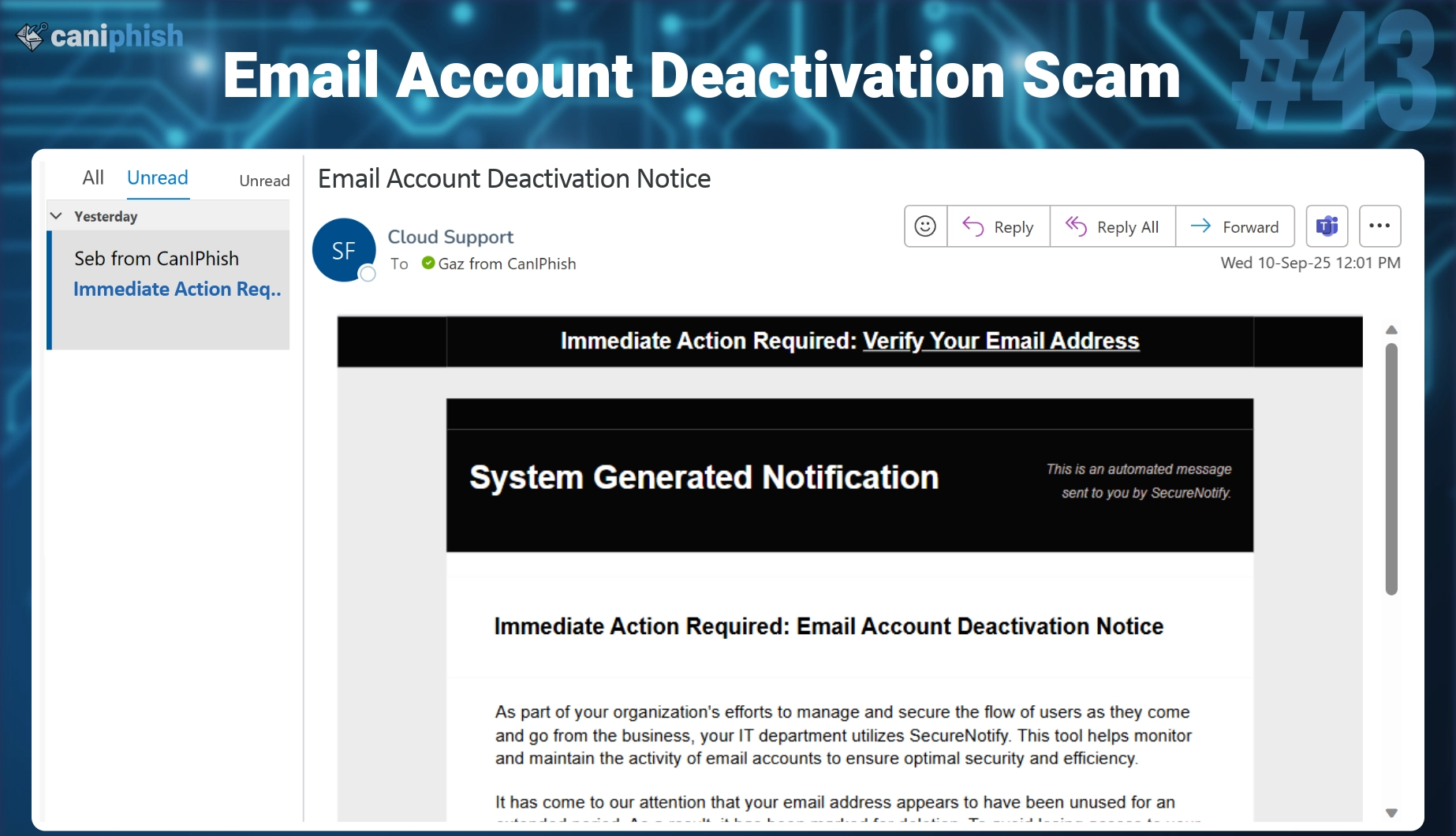
#43 Email Account Deactivation
Account deactivation scams are common phishing tactics. They exploit fear of losing access to email, files, and data. Attackers often pose as IT or security tools, sending automated-looking messages that pressure users to “verify” their account to keep it active.
- What is this email? Attackers crafted this email to look like a system-generated message from SecureNotify, claiming your email account has been inactive and is scheduled for deletion. It instructs the recipient to click a link to verify their account within 24 hours to prevent deactivation.
- Why is this email difficult to spot? The email looks like a routine automated IT notice. It's official-looking, short, and technical in tone. The branding and system-generated language make it appear legitimate. The urgency of a 24-hour deadline increases pressure, and the fear of losing access to your inbox or data pushes users to click quickly without verifying the source.
- Who is prone to falling for this phish? Any employee could be fooled, especially those who rely heavily on email for work. New hires or staff unfamiliar with the company’s real IT processes are particularly at risk. The universal fear of losing access to email and data makes this type of phishing attack broadly effective.
#42 X Content Violation
X is a popular platform widely used by individuals and businesses for real-time engagement, news sharing, and social media presence. X has become a key communication channel for influencers, brands, and support teams.
- What is this email? This phishing email claims to be from X, notifying the recipient of a supposed content violation. It urges the user to review the alleged violation by following a link, or your page may be suspended for non-compliance. The email includes X branding and styling to resemble a legitimate notification from the platform.
- Why is this email difficult to spot? The email looks like a standard policy enforcement notice, complete with branding, layout, and tone that closely mirror official X communications. It uses urgency by threatening account suspension. This is obviously a powerful motivator, especially for individuals or organizations that rely on X for outreach or brand presence.
- Who is prone to falling for this phish? This attack targets users, marketing employees, social media managers, content creators, and business owners. Anyone who relies on the platform for brand visibility or customer engagement is more likely to take the bait.
#41 Adobe Acrobat Sign Signature Required
Adobe Acrobat Sign is a widely used e-signature service that enables businesses to streamline document approvals, contracts, and agreements digitally. Adobe Acrobat Sign is especially popular for managing HR forms, NDAs, and vendor agreements.
- What is this email? This phishing email poses as a run-of-the-mill notification from Adobe Acrobat Sign, informing the recipient that their signature is required on a mutual Non-Disclosure Agreement (NDA). The message includes a link to "Review and Sign" the document and appears to be part of a regular business process involving digital signatures.
- Why is this email difficult to spot? The email flawlessly mimics the structure, and tone of legitimate Adobe communications. The branding is also spot on. For recipients in organizations that regularly use Adobe Acrobat Sign, the request feels normal and blends in with their usual workflow, making the red flags easy to overlook.
- Who is prone to falling for this phish? Executives, legal teams, HR professionals, and anyone involved in document signing or approval workflows are likely targets. This type of phishing attack is especially effective in companies that already use Adobe products.
#40 Netflix Password Expiry
Netflix is a service that requires no introduction. Originally founded as a DVD rental service in 1997, it transitioned to streaming in 2007. As of 2023, Netflix boasts approximately 238 million subscribers globally, making it one of the largest streaming platforms in the world.
- What is this email? This email claims to be from Netflix, warning the recipient that their password is due to expire soon and urging them to reset it immediately due to a purported increase in account compromises. It includes a "Reset Password" link, which is, in reality, a phishing attempt to steal Netflix login credentials.
- Why is this email difficult to spot? The email mimics legitimate security alerts from Netflix, incorporating typical language about account security and urgent action. It uses a direct and personal tone, referring to the Netflix team as "Your friends at Netflix," which can make the communication feel more authentic and trustworthy. The inclusion of standard footer links (Settings, Terms of Use, Privacy, Help Centre) similar to those in genuine Netflix emails adds to the deception, making it appear more credible.
- Who is prone to falling for this phish? Netflix subscribers, especially those who may not be aware of how legitimate password reset processes are typically handled, might be susceptible to this phishing attack.
#39 Request For Quote
Request for Quote (RFQ) phishing emails are a sophisticated scam where attackers pose as potential clients requesting quotes for services. These emails appear urgent and professional and, in this example, entice the recipient to download a malicious file.
- What is this email? This email appears to be a professional request from Yamabiko Corporation for a quote on an upcoming project, emphasizing a critical timeline and the need for a swift response. It asks for a comprehensive quote, including pricing and delivery charges, in response to an attached Request for Quotation (RFQ)
- Why is this email difficult to spot? The email is crafted to look like a typical business communication, complete with the name and position of a procurement officer and a formal tone that discusses project requirements and timelines. It includes detailed instructions and a sense of urgency, which are common in genuine business interactions. The inclusion of confidentiality notices and professional language adds to its appearance of legitimacy, making it harder to identify as a phishing attempt.
- Who is prone to falling for this phish? Business professionals, particularly those in sales, supply chain, or procurement roles, might be vulnerable to this type of phishing attack. Individuals who handle supplier communications and are used to receiving RFQs and other business documents are especially at risk.
#38 Amex Card Confirmation
American Express (Amex) is a global financial services corporation best known for its credit card, charge card, and traveler's cheque businesses. Amex cards are used by approximately 114 million cardholders worldwide, catering primarily to affluent individuals and businesses, offering premium services and rewards.
- What is this email? This email purports to be a notification from American Express, indicating that either the recipient or an authorized user has requested a new card for their account. It includes links to confirm the card request or to indicate that something is wrong, as well as a general link to sign into the account.
- Why is this email difficult to spot? The email successfully imitates the official communication style of American Express, complete with service marks, privacy policies, and contact options. It addresses security concerns directly by asking the recipient to confirm a transaction, which is a common legitimate practice, thereby enhancing its believability. The professional design and detailed footer that includes disclaimers and corporate information add layers of perceived legitimacy.
- Who is prone to falling for this phish? American Express cardholders, especially those who frequently manage their accounts online or expect communications from the company, are most vulnerable to this type of phishing attack.
#37 Venmo Payment Notification
Venmo is a digital wallet that lets users make and share payments with friends for personal use and also supports business transactions. It allows for quick transfer of money between private individuals and is increasingly used by small businesses to receive payments for services or goods, combining social networking features with financial transactions.
- What is this email? This email presents itself as a notification from Venmo, indicating that the recipient has received a substantial amount of money. It prompts the recipient to "Accept Money" through a provided link. This setup is typical of a phishing scheme aimed at capturing Venmo login credentials or other sensitive financial information.
- Why is this email difficult to spot? The email uses a plausible Venmo transaction format, including specific details like invoice numbers, payment amounts, and deadlines for accepting the money. It mimics Venmo's communication style and branding, complete with contact information and an address, making it look authentic.
- Who is prone to falling for this phish? Venmo users, particularly those who use the service for business transactions or frequently receive payments, are susceptible to this type of phishing attack. Individuals expecting payments or unfamiliar with Venmo's standard procedures for notification and payment acceptance might quickly click on the link, hoping to claim the funds, thereby falling into the phishing trap.
#36 TikTok New Device
TikTok, launched in 2016 by ByteDance, is a social media platform for creating, sharing, and discovering short videos. It is especially popular among Gen Z users. The app offers a wide range of sounds and song snippets, along with the option to add special effects and filters to videos, fostering a vibrant, creative community.
- What is this email? This email claims to be a security alert from TikTok, notifying the recipient about a login from a new device and providing a verification code to confirm the device's legitimacy. It also includes a "Reset Password" link as a precautionary step if the recipient did not initiate the login.
- Why is this email difficult to spot? The email pretends to be a security notification from TikTok, complete with a verification code and urgent security recommendations. It uses official language and formatting, adds links to supposed support resources, and even includes the correct contact details and privacy policy links, all of which make it appear more legitimate.
- Who is prone to falling for this phish? TikTok users, especially those who are active and have linked personal or business accounts, are most at risk. Users who are conscious about securing their accounts but may not be vigilant about scrutinizing the authenticity of every communication could be deceived into clicking the phishing link, thinking they are taking necessary security precautions.
#35 Google Workspace QR Code
Google Workspace, rebranded from G Suite in 2020, is a collection of cloud computing, productivity, and collaboration tools developed by Google.
Workspace aims to enhance productivity for businesses through integrated and smart collaboration tools.
- What is this email? This email is crafted to appear as a security notification from Google Workspace, claiming that the recipient's account has been suspended and requires verification through Multi-Factor Authentication (MFA). It instructs the user to scan a QR code with their mobile device, which is described as a step to unlock the account.
- Why is this email difficult to spot? The email effectively mimics the layout and language used in legitimate Google Workspace communications. It leverages the plausible scenario of requiring MFA for additional security, which is a common practice.
- Who is prone to falling for this phish? This type of phishing attack is particularly threatening to individuals in administrative roles or those who manage IT services within their organizations, as they are responsible for dealing with security protocols like MFA. These individuals may be more likely to act quickly to resolve what appears to be a legitimate security concern, especially if they believe it could impact their access or the security of the services they oversee.
#34 Sharepoint Access Request
SharePoint is a web-based collaborative platform integrated with Microsoft Office. Primarily used by businesses for document management and storage, SharePoint supports an array of functionalities, including custom web applications and workflow automation.
It caters mainly to enterprise users, enhancing teamwork through its collaboration and information-sharing tools.
- What is this email? This email is a request for access to a SharePoint resource. It provides options to "Accept" or "Decline" the access request and includes details of the bogus requester, Sonny Smith, with an email purportedly from the same company domain.
- Why is this email difficult to spot? The email utilizes a common legitimate function of SharePoint—access requests—which employees may regularly encounter in a workplace that uses SharePoint for document and resource management. The format is concise and mimics the style of genuine SharePoint notifications, complete with company-specific URLs and names that add an air of authenticity.
- Who is prone to falling for this phish? Employees who frequently use SharePoint in their organizational workflows are particularly vulnerable to this type of phishing attack. Those not vigilant about verifying the legitimacy of access requests or those accustomed to routinely granting such permissions may quickly respond to the email without proper scrutiny.
#33 Stripe Password Update
Stripe, launched in 2010, is a technology company that offers payment processing solutions for online and mobile businesses, making it easier to accept payments, manage transactions, and build new business models. Known for its developer-friendly platform, Stripe supports businesses in over 120 countries.
- What is this email? This email is disguised as a notification from Stripe, informing the recipient that their Stripe account password has been updated. It provides a link for the recipient to reset their password if they did not initiate this change. The email also directs them to check their account's security history and contact support if they spot any suspicious activity. However, the reset link is a phishing attempt designed to steal Stripe credentials.
- Why is this email difficult to spot? The email leverages a realistic scenario that could occur in the normal operations of an online payment platform like Stripe. It includes detailed instructions on how to respond to the supposed password change, mimicking legitimate customer support protocols. The professional tone and inclusion of links to purportedly legitimate Stripe pages further blur the lines between authentic and fraudulent communications.
- Who is prone to falling for this phish? Stripe users, particularly small business owners, freelancers, or individuals who rely heavily on Stripe for business transactions, may be particularly susceptible to this type of phishing. The urgency of a security breach involving financial accounts can cause panic, leading users to act hastily by clicking on phishing links without verifying their authenticity in an effort to secure their financial data.
#32 1Password Password Change
1Password is a well-known password manager that provides secure storage for passwords, software licenses, and other sensitive information. It helps users create strong passwords and access them on various devices. Known for its strong encryption and user-friendly interface, 1Password enhances online security and simplifies login processes.
- What is this email? This email claims to be from 1Password, alerting the recipient that the password for their 1Password account has been changed. It includes an urgent call to action, providing a link for the recipient to reverse the change if they did not initiate it.
- Why is this email difficult to spot? The email creates a sense of urgency and plays on the fear of unauthorized account access, which can prompt immediate action from the recipient. The professional layout, complete with a realistic footer containing contact information and an address, mimics legitimate corporate communications from 1Password, making it harder to identify as fraudulent.
- Who is prone to falling for this phish? Users of 1Password, particularly those who may not be highly tech-savvy or those who may panic upon reading about an unauthorized change, are vulnerable to falling for this phishing attempt. The urgency and direct call to action exploit natural security concerns and can lead to hurried decisions without proper verification of the email's authenticity.
#31 Xero Statement
Xero is a cloud-based accounting software for small to medium-sized businesses. It provides tools for managing invoicing, bank reconciliation, payroll, and reporting, among others. Known for its real-time financial overview and integration capabilities, Xero simplifies accounting processes and enhances financial visibility.
- What is this email? This email is a notification from Xero, the accounting software company, inviting the recipient to download a Quarterly Profit and Loss Statement. It includes details on how to manage access levels within Xero, which could be seen as providing additional security advice.
- Why is this email difficult to spot? The email cleverly uses a legitimate business scenario—sharing financial documents—that a user might expect as part of routine financial management. The inclusion of typical elements such as privacy statements, unsubscribe links, and references to common Xero user roles adds a layer of authenticity that could easily fool users into thinking the email is genuine.
- Who is prone to falling for this phish? Business owners, accountants, and administrative staff who regularly use Xero for financial management might be particularly susceptible to this phishing attack. The professional context and the direct relevance of the content (a profit and loss statement) to their daily operations make it more likely that they would interact with the email without suspicion, especially if they are expecting such documents.
#30 GitHub OAuth App
GitHub, launched in 2008, is a platform for version control and collaboration. It allows developers to manage and store their code projects, track changes, and collaborate with others.
- What is this email? This email imitates a notification from GitHub, informing the recipient that a third-party OAuth application (AWS CodeBuild) has been authorized to access their account with specific permissions. It includes phishing links leading to GitHub settings and support pages aimed at stealing GitHub credentials or deploying malware.
- Why is this email difficult to spot? The email appears legitimate due to its use of technical jargon familiar to GitHub users and detailed references to OAuth permissions, which could be part of a typical workflow for developers using third-party integration. The inclusion of specific URLs that resemble GitHub’s domain structure adds credibility and might deceive users into believing they are accessing official GitHub pages.
- Who is prone to falling for this phish? Developers and users who frequently interact with GitHub and third-party applications are particularly vulnerable to this type of phishing attack. These users may be accustomed to receiving notifications regarding application permissions and might not question the authenticity of such emails, especially if they are actively using or expecting communications from integrations like AWS CodeBuild.
#29 Quarantined Email
Quarantined emails are emails that an email security system has set aside because they are suspected to be spam, contain malware, or violate certain email policies. These emails are isolated from the user's inbox to prevent accidental access and potential harm.
It's good practice to check your quarantined mail periodically. Doing so helps ensure that legitimate emails are not mistakenly flagged and missed.
- What is this email? This phishing email masquerades as a notification from the organization's spam filtering software. It prompts employees to sign into their quarantine mailbox to review seven suspected phishing attacks, leveraging a bogus sender profile for authenticity.
- Why is this email difficult to spot? Checking quarantined emails is routine, making this email seem like a standard procedure. It also injects urgency by stating that the user has only seven days to act, aiming to rush them into bypassing their usual critical thinking.
- Who is prone to falling for this phish? System administrators, particularly those lacking experience or training in detecting phishing attempts, are likelier to fall for this scam. Their familiarity with email security processes can ironically make them less cautious about such seemingly routine notifications.
#28 Instagram Verification
Instagram, launched in 2010, is a photo and video-sharing social networking service that allows users to post content, interact through likes and comments, and explore curated feeds. It has a strong emphasis on visual aesthetics and storytelling, significantly influencing social media trends and online marketing.
- What is this email? This email impersonates a security alert from Instagram, notifying the recipient about a suspicious login attempt from an unusual location and device. It provides a fake phishing link for the recipient to secure their account.
- Why is this email difficult to spot? The email mimics genuine security alerts that platforms like Instagram send when there's an unusual login attempt. It uses specific details such as device type, browser, and location to appear legitimate. The professional tone and inclusion of an actual address and branding associated with Instagram further mask its fraudulent nature.
- Who is prone to falling for this phish? Instagram users who are vigilant about their account security but may not be familiar with the nuances of phishing tactics are most at risk. The email exploits the user's immediate concern over unauthorized access, prompting a quick reaction to secure their account—thus leading them to inadvertently provide their credentials to the attacker.
#27 Facebook Verification
Facebook, launched in 2004 by Mark Zuckerberg, is a social networking service that allows users to connect and share with family and friends online. Originally designed for college students, it has grown into one of the world's leading social media platforms, impacting global communication and media consumption.
- What is this email? This email poses as an urgent security notification from Facebook, claiming that a significant breach has impacted almost 50 million accounts, including that of the recipient. It insists on immediate action to change the password through a provided "Reset password" link.
- Why is this email difficult to spot? The difficulty in identifying this email as a phishing scam stems from its realistic portrayal of a credible security threat—a scenario that Facebook has experienced in the past. The email uses technical language and the name of an authoritative figure within the company, enhancing its legitimacy. Furthermore, the email taps into the recipient's fear and urgency to secure their personal information, which can cloud judgment and lead to hasty actions.
- Who is prone to falling for this phish? Any Facebook user, particularly those who are not regularly updated on legitimate security practices or news, might fall for this phishing attempt. Users who are aware of past real security breaches at large companies may be even more inclined to believe the authenticity of the email and follow the deceptive instructions without sufficient scrutiny.
#26 Dropbox Verification
Dropbox is a well-known file hosting service that offers cloud storage, file synchronization, and client software. Launched in 2007, it enables users to create a special folder on their computers, which Dropbox then synchronizes so it appears the same regardless of the device used.
- What is this email? This email masquerades as an urgent notification from Dropbox, asserting that the recipient's account has been inactive and is on the verge of being closed. It pressures the user to act swiftly to save their account by signing in through a provided link, which is likely malicious.
- Why is this email difficult to spot? The difficulty in recognizing this email as a phishing attempt stems from its plausible scenario of account inactivity leading to closure, a policy some real services might follow. The email's professional tone and concise language mirror legitimate corporate communication, making it seem authentic at first glance.
- Who is prone to falling for this phish? Individuals who use cloud storage services like Dropbox for personal or business purposes could be particularly vulnerable to this phishing attempt. The urgency conveyed by the threat of losing important documents can prompt hasty actions, especially if the recipient has not recently checked their account activity and fears data loss.
#25 Zoom Invite
When the pandemic enveloped the globe, transforming home spaces into offices, Zoom rapidly evolved into a household name, becoming synonymous with the work-from-home culture.
Given its widespread use, particularly among remote workers, Zoom has become a prime target for scammers, who exploit its popularity to phish unwary employees.
- What is this email? Adopting Zoom's familiar branding, this email announces a "Quarterly All Hands" meeting, urging users to confirm their account. It directs them to a button, which leads to a fraudulent Zoom login page.
- Why is this email difficult to spot? Zoom's widespread use across various organizations makes this email seem routine, even for employees whose companies don't primarily use Zoom. Paired with a phony Zoom login page and a subtly disguised sender profile, spotting the deception is challenging.
- Who is prone to falling for this phish? Employees accustomed to Zoom meetings, both within and outside their organization, are prime targets.
#24 Udemy Free Credits
Udemy is an online learning platform for professional adults and students. It was founded in May 2010 and has become one of the leading platforms in the online learning space.
- What is this email? Utilizing the recognizable Udemy branding and design, this cunning email informs employees that they must log in to claim the USD$200 credit. The catch is in the login attempt.
- Why is this email difficult to spot? Expertly mimicking Udemy's format, the email includes a personalized message and a straightforward path to claim the credits. The simplicity of just clicking a "Claim Udemy Credits" button adds to its deceptive allure.
- Who is prone to falling for this phish? Employees in companies that use Udemy for training purposes or offer learning incentives are particularly susceptible to this phishing attempt. Their familiarity with receiving benefits through Udemy makes the scam more believable.
#23 Bamboo HR Employee Benefits
BambooHR is a human resources software service launched in 2008. It provides online HR tools primarily for small and medium-sized businesses, focusing on personnel data management, hiring, onboarding, compensation, and culture. It's known for its user-friendly interface and comprehensive HR features.
- What is this email? This email purports to be a notification from BambooHR, informing the recipient that their company benefits have been updated. It encourages the recipient to click on a provided link to view these benefits, a typical action for such a notification.
- Why is this email difficult to spot? This email's challenge in detection lies in its seemingly harmless invitation to view something as routine as company benefits—an action employees might often perform. The email uses a positive tone and a professional layout, mimicking genuine communications from HR software platforms, which adds to its believability.
- Who is prone to falling for this phish? Employees accustomed to receiving regular updates about HR matters such as benefits, payroll changes, or policy updates are especially susceptible to this type of phishing. The familiar context and the direct call to action exploit the routine administrative processes that employees expect and trust, making them less vigilant about verifying the authenticity of the email.
#22 Salesforce Password Expiry
Salesforce is a leading cloud-based software company primarily known for its customer relationship management (CRM) service.
Given its widespread use and prominent position in the business software landscape, Salesforce is a key player in many companies' digital transformation.
- What is this email? This phishing email plays the familiar tune of a "password expiring soon" alert. It warns users they have only three days to reset their password. Clicking the 'reset password' button or any link within the email directs them to a bogus company login page.
- Why is this email difficult to spot? The commonality of legitimate password expiry emails adds to the confusion. Coupled with convincing Salesforce branding, distinguishing this fake from the real deal becomes challenging.
- Who is prone to falling for this phish? Employees in organizations that utilize Salesforce are particularly susceptible. Familiarity with receiving such password-related communications from Salesforce makes them prime targets for this phishing attempt.
#21 Return to Work Survey
Scammers exploit global events like COVID-19 to blend malicious emails with legitimate corporate communications. As companies return to office work post-pandemic, these phishing attempts find fertile ground.
With the rise in QR code usage for payments, menus, and information sharing, especially post-pandemic, there has been an increase in QR code phishing attempts. Cybercriminals capitalize on the ubiquity and trust in QR codes to execute various scams.
- What is this email? This email urges employees to download and return an attached document, framed as a survey, for feedback on returning to the office. It taps into the innate desire to be heard and share opinions about this significant transition.
- Why is this email difficult to spot? The email's authenticity is bolstered by personalized content and a lack of obvious red flags. Only a closer inspection of the sender's profile reveals its true, malicious nature.
- Who is prone to falling for this phish? Employees in organizations currently navigating the shift back to office work are prime targets. Additionally, those who value having their voices heard or hold strong opinions about workplace policies might be less cautious.
#20 Win An iPhone 15 QR Code
QR code phishing, also known as "quishing," poses significant dangers due to the growing popularity and convenience of QR codes. We just had to include one in the list!
With the rise in QR code usage for payments, menus, and information sharing, especially post-pandemic, there has been an increase in QR code phishing attempts. Cybercriminals capitalize on the ubiquity and trust in QR codes to execute various scams.
- What is this email? This email, seemingly from HR, promotes a company competition with an iPhone 15 as the prize. All you need to do is scan the QR code to get started...
- Why is this email difficult to spot? An exciting contest combined with the ease of entry via a QR code makes this phishing email particularly convincing. Its expertly crafted appearance and feel closely mimic legitimate corporate communications.
- Who is prone to falling for this phish? Employees drawn to the thrill of winning, especially tech enthusiasts eager for the latest gadgets, are most likely to be enticed into scanning the QR code without due caution, making them prime targets for this phishing tactic.
#19 Lyft Free Rides
Lyft is an American ride-sharing company based in San Francisco, California. Founded in 2012, Lyft offers various services, including car rides, a bicycle-sharing system, and a food delivery service. The company is known for its mobile app, which allows customers to book a ride with a nearby driver using their smartphone.
- What is this email? Disguised as a message from HR, this email entices employees with the offer of 10 free Lyft rides as part of a company initiative. Clicking the phishing link leads to a prompt for company login credentials.
- Why is this email difficult to spot? Blending a typical company incentive scenario with Lyft's branding, the email convincingly bypasses suspicion for those not well-versed in spotting such deceptions.
- Who is prone to falling for this phish? Employees in companies that routinely use Lyft or offer perks like freebies are particularly susceptible to this convincing phishing scheme.
#18 Qantas Frequent Flyer
The Qantas Frequent Flyer program is a customer loyalty program offered by Qantas Airways, Australia's largest airline. This program rewards frequent flyers and encourages customer loyalty towards Qantas and its partners.
- What is this email? This email mimics an alert for unusual account activity. The email presents two options: "No, this wasn't me" and "Yes, this was me." Both buttons deceptively lead to a fake Qantas login page.
- Why is this email difficult to spot? Its severity makes it alarming, potentially triggering panic. In haste to secure their account, employees often overlook the usual checks to identify a phishing attempt.
- Who is prone to falling for this phish? Those personally using Qantas Frequent Flyer or employees in businesses that do are especially vulnerable to this well-crafted scam email.
#17 Fake Meeting
Google Meet is a powerful video conferencing tool that many businesses and individuals around the globe commonly use. Due to its popularity, most employees have seen this type of "Join The Meeting" email, making it a popular choice as a phishing email.
- What is this email? Posing as a Google Meet invite, this email tricks employees into clicking a link that leads to a fraudulent site designed to harvest their credentials.
- Why is this email difficult to spot? Mimicking a legitimate and familiar format creates urgency with a 'now' timing and includes the employee's email in the body, enhancing its authenticity.
- Who is prone to falling for this phish? Individuals who overlook verifying the sender's information are particularly susceptible. Additionally, organizations that frequently use Google Meet as their primary video conferencing tool face a heightened risk of falling prey to this scam.
#16 Western Union Wire Transfer
The Western Union Wire Transfer Scam is a sophisticated phishing attack that leverages Western Union's reputation. This scam preys on the trust and urgency typically associated with wire transfers.
- What is this email? This deceptive email cunningly impersonates an official communication from Western Union, luring the recipient into believing they are about to receive a substantial sum of money. The email prompts the unsuspecting individual to confirm receipt of this amount by completing an attached document. Additionally, it cleverly includes a link leading to a fraudulent Western Union login page.
- Why is this email difficult to spot? The difficulty in identifying this email as a scam arises from its expert use of Western Union's trusted reputation and the email's personalized information tailored to the recipient.
- Who is prone to falling for this phish? Virtually any employee who finds this email in their inbox risks falling prey to this phishing attempt. The risk is significantly heightened in organizations that frequently use Western Union for business transactions.
#15 New Years Bonus
As the year winds down and the festive spirit takes over, the New Year's Bonus Scam emerges as a particularly insidious threat. This scam plays on the expectations and excitement surrounding end-of-year bonuses, a time-honored tradition in many organizations.
- What is this email? This email, disguised as an HR announcement, tempts employees with a large bonus, luring them to complete a form. Its unusual nature doesn't deter 42% of employees, swayed by the cash promise.
- Why is this email difficult to spot? This text-based email cleverly uses personalized details, creating urgency and authority. Combined with the promise of financial gain, it embodies classic phishing tactics, making it difficult to spot.
- Who is prone to falling for this phish? Employees who don't pause to scrutinize the email's authenticity, especially in their eagerness for the bonus, are most susceptible to this scam.
#14 Office Holiday Party
Who doesn't love an office party? This generic email has no personalization yet still fools many employees. Its innocuous content ensures that no red flags are raised, which means it's extremely dangerous.
- What is this email? A seemingly innocent email poses as Google Drive, inviting you to an "Office Holiday Party" with a simple "Open" button. Clicking leads to a phishing site aiming to snatch your Gmail credentials.
- Why is this email difficult to spot? Leveraging Google's trusted brand and our innate curiosity, this email contains no personalization. Its simplicity and harmless appearance make the email an effective phishing attack.
- Who is prone to falling for this phish? Curious individuals, drawn in by the mention of an office party, are most likely to fall for this cleverly disguised phishing attempt.
#13 Job Opportunity
In an age where career growth and job changes are commonplace, the allure of a high-paying job offer can be irresistible. This is what cybercriminals capitalize on in the Job Opportunity Scam.
- What is this email? Disguised as an offer from HR, this email dangles a job with a hefty salary and generic requirements and asks you to fill out and return an attached file.
- Why is this email difficult to spot? The email's cunning lies in its personalization and simplicity, addressing you by your full name, making it seem credible and hard to doubt.
- Who is prone to falling for this phish? This email is generic and has proven to be extremely difficult to spot. Any employee curious or motivated by financial gain is prone to falling for this phish.
#12 Bank of America Suspended Account
Bank of America is one of the largest financial institutions in the United States of America. It’s used by both a mixture of consumer and business customers and provides a wide variety of banking services.
This has made it a popular target for cyber criminals who typically utilize phishing to either steal banking credentials or install banking malware. Like many banks, Bank of America periodically sends out emails to their customer base, whether marketing-related, transactional, or even scheduled.
- What is this email? This email is masquerading as a Bank of America suspended account notification. It’s notifying the recipient that unusual activity has been detected on their account, and accordingly, an account hold has been put in place. To remedy this, the email tries to entice the recipient to click a button, which then leads to a phishing website.
- Why is this email difficult to spot? This email uses a high degree of personalization, using the recipient's first and last names within the email body. Further to this, it’s easy for this email to mix in with the flurry of legitimate emails that Bank of America periodically sends out.
- Who is prone to falling for this phish? Employees who use Bank of America as their banking institution. Typically, this will only be for a subset of employees located in the United States of America.
#11 DocuSign Signature Request
DocuSign is a popular online service for handling digital agreements. In many cases, the request to exchange and sign an agreement is sent through email. Because of this, DocuSign-themed scams are enticing for attackers to use.
- What is this email? This email is masquerading as a DocuSign signature request, where the recipient is asked to click on a link to review and sign a document.
- Why is this email difficult to spot? It’s not uncommon that DocuSign signature requests come through at unexpected times. It could be that you need to sign off that you’ve read a certain policy, performed an annual training, or done a variety of other actions. Because of this, recipients of DocuSign emails have become trained to expect unsolicited emails appearing to come from DocuSign.
- Who is prone to falling for this phish? Any employee is prone to this phishing email.
#10 Microsoft OneDrive File Share
Microsoft OneDrive is a core product within the Microsoft 365 Suite of products. It’s used for both cloud-based file storage and collaboration between colleagues, partners, and customers. When a file is shared using Microsoft OneDrive, the notification arrives through email, which explains why this scam is so successful.
- What is this email? This email is masquerading as a Microsoft OneDrive file share email. It notifies the recipient that they’ve just been sent a Word document relating to employee performance reports and prompts the recipient to click a link in the email to view the document.
- Why is this email difficult to spot? While this email contains no personalization, it’s trying to invoke an emotional response in the recipient because this file has likely been shared with them by accident and contains sensitive information that they would want to know about. If the recipient is a little bit too curious, they’ll click the phishing link without properly analyzing the email.
- Who is prone to falling for this phish? Employees who use Microsoft OneDrive will be particularly susceptible to this email, but because Microsoft OneDrive is frequently used to share files with non-Microsoft users, any employee could be susceptible to this phish.
#9 Microsoft Teams Missed Message
Compromise Rate: 31% | Personalization: First Name | Attack Type: Credential Compromise (Link)
Microsoft Teams is a favorite among large businesses. It includes a plethora of functionality and integrates with a wide variety of Microsoft Office products.
When adopted by a business, typically, every employee will gain access to the Microsoft Teams Platform, so it comes as no surprise this email ranks number 9 on the list.
- What is this email? This email is masquerading as a Microsoft Teams missed message notification. It’s notifying the recipient that a team member tried to contact them about an upcoming leave request they’ve made. It then prompts the recipient to message the sender back by clicking a button.
- Why is this email difficult to spot? When someone is away from their desk or misses a message, it’s common to get an email from Teams keeping them updated on everything that’s happened in their absence. While this email contains no personalization, it fits into the theme of generalized notifications that Microsoft Teams sends out and can easily be overlooked as just another legitimate notification.
- Who is prone to falling for this phish? Any employee who uses Microsoft Teams.
#8 Slack Password Reset
Compromise Rate: 32% | Personalization: None | Attack Type: Credential Compromise (Link)
Slack needs no introduction. It’s one of the most popular communication and collaboration platforms in the world.
Employees use Slack every day to communicate with their colleagues and even customers. Receiving email notifications from Slack is a common occurrence, making it no surprise that this phish is as effective as it is.
- What is this email? This email is masquerading as a Slack password reset notification. It’s notifying the recipient that their password is due to expire in the next 24 hours, and a new password needs to be set.
- Why is this email difficult to spot? While this phishing email contains no personalization, it doesn’t need it. The email instead relies on the urgency of the request to entice the recipient to take immediate action. This action takes the form of a phishing link, which is the primary call to action.
- Who is prone to falling for this phish? Any employee who uses Slack.
#7 LastPass Suspicious Login
With the average person using more and more online services, it’s become increasingly difficult to keep track of all the passwords used to log in to them.
While many people are enticed to re-use passwords, the ever-growing number of data breaches has made a lot of people aware of the risks associated with credential re-use. If an attacker steals your credentials from a data breach for one online service you use, they could potentially log in to all the services you use!
It’s for this reason that password managers such as LastPass have become so popular!
- What is this email? This email is masquerading as a LastPass suspicious login notification. It’s notifying the recipient that someone just used their master password to log in from an unrecognized location.
- Why is this email difficult to spot? For anyone who uses a password manager, receiving an email such as this is their worst fear. Password managers essentially hold the crown jewels and store all the sensitive secrets and credentials for anyone who uses them. With this in mind, this email is designed to invoke a fearful response in the recipient, causing them to interact with it without applying critical thinking. The additional use of light personalization increases the realistic look and feel of this email.
- Who is prone to falling for this phish? Any employee who uses the LastPass password manager.
#6 FedEx Shipment
Expecting to receive a package? The interesting thing about being the receiver of a package is that you often aren’t the one who chooses who the actual courier is. In many cases, you just receive a notification from the courier, and you have to trust that what they’ve sent matches with what you’re expecting.
It’s the unexpected nature of these notifications that makes this phish so dangerous! Forgive the pun. Let’s unpack this email and learn what makes it so devious.
- What is this email? This email is masquerading as a FedEx shipment tracking notification. It advises the recipient that they have a package in transit and entices them to click the tracking link.
- Why is this email difficult to spot? It’s not an uncommon scenario for packages to be received without prior notification. It could be a present from someone, a gift from an individual's workplace, or perhaps even a delivery that’s just been forgotten. These factors can make a normally unexpected email seem normal. Couple that with some personalization in the form of the recipient's first name, and we have an effective scam.
- Who is prone to falling for this phish? Any general consumer or employee is vulnerable to this phish.
#5 HR Policy Violation
The dreaded email from Human Resources (HR). With an average of 35% of employees being compromised, we recommend using this phish with care!
- What is this email? This email is masquerading as an email from the HR team, notifying the receiving employee that they’ve violated company policy and viewed inappropriate material on their work computer.
- Who is prone to falling for this phish? Due to the general nature of the phish, any employee could fall for it.
- Why is this email difficult to spot? This email can send shivers down the spine of anyone who receives it. It leaves the recipient questioning, what was it that I did? How bad was it? Did I run the wrong search on the wrong computer? In any case, it leaves the recipient with a feeling that they need to prepare their defense, and the first part of that is viewing the purported evidence. Adding an additional layer of deviousness, this email contains a phishing link, a phishing attachment, and a high degree of personalization.
#4 Prezzee Gift
Do you love gift cards? Well, so do cyber criminals! It provides them with a means of stealing money from unsuspecting victims without the hassle of needing to launder the money through banks or credit card companies.
Prezzee is a popular service used by consumers and businesses to send and manage gift cards. This makes it a popular target for financially motivated attackers looking to scam people.
- What is this email? This email is masquerading as Prezzee. Specifically, it appears to be a company-issued gift card that’s being provided to the receiving employee due to their high performance.
- Why is this email difficult to spot? This email contains an element of personalization with the receiving employee's first name and the name of the company they work for being used within the email body. This email also relies on inciting excitement within the receiving employee, which could cause them to bypass the critical thinking normally applied to an unexpected email.
- Who is prone to falling for this phish? Any employee who is familiar with the Prezzee gift card service or views themselves as a high performer and deserving of a reward, raise, or other form of bonus.
#3 Gmail Blocked Login
Coming in third, we have another Google-themed scam, which compromises 38% of employees on average!
Google Mail, otherwise known as Gmail, is an incredibly popular email collaboration tool that is used by both consumers and businesses. It’s become so popular, predominantly due to its accessibility, cost, and native integration with other Google products.
While this makes it a great tool for its users, its sheer popularity makes it an attractive target for phishing emails.
- What is this email? This email is masquerading as Gmail. More specifically, it appears to be a security notification that advises the recipient that Google just blocked a suspicious login attempt and that the recipient's password has potentially been compromised.
- Why is this email difficult to spot? While this email contains no personalization, the sheer urgency and fear it sparks in recipients is enough to make it difficult to spot. This email relies on recipients having an emotional response and not critically analyzing the email.
- Who is prone to falling for this phish? Anyone who uses Gmail or other Google-provided products.
#2 Jira Notification
Jira is one of the most popular issue and project tracking tools on the market. Employees who use it have come to love the service it provides because it's designed to help teams collaborate and make everyone’s life easier.
The downside of this is that it makes it a prime target for attackers to use for phishing!
- What is this email? This email is masquerading as Jira, the issue and project tracking software. Specifically, the email appears to be a Jira notification notifying the recipient that they’ve been assigned a new task.
- Why is this email difficult to spot? This email contains a high degree of personalization, including the employee's first name and last name. This personalization, along with the usage of Jira logos, terminology, and the transactional nature of the email, makes it particularly difficult to spot.
- Who is prone to falling for this phish? Software developers, project managers, product managers, and IT administrators would be particularly susceptible to this type of phishing email. As these employees typically have elevated access within businesses, this phishing email is particularly attractive to cyber criminals.
#1 Google Drive File Share
With an average of 54% of employees being compromised, this Google Drive scam is the most dangerous of the lot!
This should come as no surprise. Employees who use Google Workspace typically receive Google Drive file-share emails on a daily basis. An email such as this is uniquely positioned to not raise any alarm bells from the employee viewing it while still being engaging enough that they’re enticed to click on the payload.
- What is this email? This email is masquerading as the Google Drive service. Specifically, it appears to come from the HR team and entices individuals to click on a link that leads to an updated company organizational chart.
- Why is this email difficult to spot? By masquerading as a commonly used service, it can easily blend into the mix of other emails an employee would receive on any given day. It additionally introduces a layer of urgency by indicating that a sudden change has taken place, and it's in the employee's best interest to find out what changes took place.
- Who is prone to falling for this phish? Any employee who uses Google Workspace.
Wrapping Up
When viewing each email, ask yourself whether it applies to your organization based on industry, geographic location, and enterprise software in use. Additionally, consider whether the phishing emails are something your employees would benefit from in terms of their skill level. There's no point in sending your employees an extremely difficult phishing email when they're at a beginner skill level - the indicators they should look for will go over their heads.
With these factors in mind, pick the best phishing emails that are uniquely suited to your organization!