How To Create A Phishing Email In 7 Steps

Understanding how to create and deliver realistic phishing emails is a topic that’s shrouded in mystery.
In this blog, we’ll walk through the step-by-step process of creating phishing emails, explore delivery methods, analyze email filtering technologies, examine evasion techniques, demonstrate domain spoofing, and provide actionable measures to mitigate against phishing.
What You'll Learn In This Article.
- What services cyber criminals commonly create phishing emails against.
- How to create and deliver phishing emails.
- How to use real-world phishing techniques such as sender address spoofing.
- How to overcome the challenge posed by email filters, which commonly detect and block phishing emails.
Prerequisite: Understand The Types Of Phishing Emails
Let’s get a better understanding of the phishing email templates used by attackers.
Phishing Emails For Financial Institutions
Cybercriminals frequently impersonate banks, credit card companies, and payment processors. Their goal is to trick victims into sharing sensitive data, such as account credentials, financial information, or credit card details.
Example: A phishing email claiming to be from a renowned bank requesting immediate verification of recent credit card activity. The email includes a link to a spoofed login page designed to capture user credentials.
Phishing Emails For Social Media Platforms
Popular social media platforms like Facebook, Twitter, and Instagram are often impersonated by cybercriminals. Their goal is to trick victims into divulging their login credentials or personal details.
Example: A deceptive email appearing to be from Facebook, notifying users of a recent breach and urging them to reset their password. The email includes a link that leads to a malicious website designed to steal login credentials.
Phishing Emails For E-Commerce Websites
Cybercriminals frequently impersonate well-known online retailers, such as Amazon, eBay, and Groupon. Their goal is to trick victims into sharing credit card details, login credentials, or other personal information.
Example: An email posing as an order confirmation from Amazon, stating that the recipient needs to click on a link to track their recent purchase. The link leads to a fake website designed to harvest user data.
Phishing Emails For Professional Networks
Cybercriminals may impersonate professional networking platforms like LinkedIn or Yammer with the goal of tricking victims into clicking on malicious links, revealing their account credentials, or even tricking them into accepting fake job opportunities to steal money from them through complex trust scams.
Example: An email impersonating LinkedIn, claiming that a password reset request has been initiated and the recipient needs to verify the code to set their new password. The link leads to a phishing page requesting login credentials.
Step 1. Defining Your Goals
Before attempting to create a phishing email, you need to clearly establish the objectives of your phishing campaign. Is it to test employee awareness? Assess vulnerabilities within your organization? Or gather credentials or other sensitive information as part of a red-team exercise. Perhaps it’s a mixture of everything.

Step 2. Conducting In-Depth Research
To create a convincing phishing email, you need to understand your intended audience. This could include researching the services they use on a day-to-day basis, knowledge of their geographic area, and even understanding the internal organizational structure to know whom certain employees report to and the business function they operate within. Once these factors are known, you can begin creating the phish.
You should also sign up for the service you intend to impersonate and look at the transactional and marketing-related emails they send. Test out functionality such as initiating a forgotten password request, account lockout scenario, and setting up multi-factor authentication to learn about their designs, logos, and writing styles.

Step 3. Creating An Engaging Email
Based on the research performed, you should now have at least one email that you can alter for phishing purposes. This could involve slight alterations to make the email more convincing and urgent. You need to use language and formatting that closely resembles the legitimate email. Ensure that logos, branding, and visual elements in the email are unchanged or appear authentic.
For example, suppose you’re targeting an online banking service. You’ll want to use a subject line that includes urgency, such as "Important Security Alert: Immediate Action Required." In the body, adopt a tone of concern, emphasizing the need for the victim to verify their account details to prevent unauthorized access.
Tip: See the CanIPhish Phishing Email Simulator, which has a library of 100+ phishing emails for inspiration.
Step 4. Embedding The Payload
Cybercriminals often use disguised hyperlinks to trick victims into clicking on malicious phishing websites. To do this, you’ll need to create phishing links that closely resemble the legitimate service's domain. This could involve the use of lookalike domains, sub-domains, and even complex URL query string structures that obfuscate the actual domain in use. Additionally, attachments, such as PDFs or Office documents, can be used to exploit vulnerabilities or encourage victims to enable macros, which can then facilitate code execution on their device.

Step 5. Selecting An Email Provider
You’ll need to choose an email provider that suits your needs and allows you to send without interruption. Now, if you’re performing highly targeted spear-phishing on a small number of victims, you can likely use a provider like Gmail or Yahoo. However, if you’re conducting larger campaigns, such as targeting an entire organization, you’ll need more control over the email infrastructure to improve deliverability. Additional factors that may also be considered include ease of use, customization options, and the likelihood of the provider banning you from using their service.
Step 6. Purchasing A Phishing Domain
You’ll need to register a domain name that closely resembles the impersonated service's domain. A variety of domain registrars can be used for this, such as AWS Route53, GoDaddy, and much more. These providers will outline domain availability and even provide recommendations and domains that are available that closely resemble the service provider’s domain.
Step 7. Configuring The Phishing Infrastructure
Depending on the complexity of your campaign, you may need to set up additional infrastructure, such as mail transfer agents (MTAs) and email relay services. You’ll then need to configure the DNS settings of your newly purchased domain to ensure email authentication protocols like Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) are configured. These measures help improve deliverability and phish click rates.
CanIPhish has created a tool called CanIBeSpoofed, which assists with setting up SPF records, you can also use a tool such as MXToolBox to assist with this.
Leveraging Domain Spoofing Techniques
Cybercriminals may use domain spoofing to make phishing emails appear more legitimate. These emails impersonate trusted domains by abusing a weakness in the way their email authentication records have been configured.
This could involve forgery of the “From” field in the email header to display a fake sender address. SPF is designed to prevent this type of spoofing. Additionally, attackers could use an advanced spoofing technique known as spf-bypass, which involves a misalignment between the Mail Envelope from address “SMTP.MailFrom” and email header “From” address. DMARC is designed to prevent this type of spoofing.

Cybercriminals will typically use open-source intelligence (OSINT) to find potential domains to abuse for spoofing. There are a variety of domain reputation tools that attackers can use to discover and automatically analyze domain SPF and DMARC records to discover vulnerabilities that can be abused.
Another much simpler method of spoofing is the abuse of sender display names, which don’t have any email authentication protections. Often, this is used in conjunction with spoofed “From” addresses.
The Challenge Posed By Email Filters
Email filters play a crucial role in detecting and blocking phishing emails. They utilize various techniques, such as signature-based filtering, heuristics, and machine learning, to detect suspicious emails. However, these detection mechanisms aren’t perfect, and cyber criminals are continuously refining their tactics to avoid detection. Some of these techniques include:
- Polymorphic Attacks: Generating multiple variants of the same email to avoid detection based on known signatures. By altering content, subject lines, and attachments, cybercriminals can bypass traditional detection methods.
- Image-based Text: Embedding text within images helps cybercriminals bypass content-based filters that analyze text in the email body for malicious keywords or URLs. By converting text into an image, cybercriminals can deceive filters and increase the chances of successful delivery.
- URL Obfuscation: Cybercriminals employ techniques like URL encoding, URL shortening services, or redirectors to make malicious URLs appear legitimate. These tactics make it challenging for filters to recognize and block malicious links.
-
Website Redirection: Phishing campaigns may include unique URLs within each phishing email. If a unique URL is found to open a phishing link too fast, from a certain IP, or with a certain user agent string, the website may fail to load. This method prevents the detection of phishing websites where sandboxing is in use.

- Zero-day Exploits: Exploitation of vulnerabilities in email clients or servers that have not yet been patched by software providers. Cybercriminals can leverage these vulnerabilities to bypass email filters and deliver their malicious payloads.
If you're looking to deliver phishing emails as part of a red-team engagement, you'll need to implement some of the techniques listed above to ensure your emails aren’t blocked by email filters.
Managing The Outcome
Once you’ve created the phishing email, set up the phishing infrastructure, and configured any additional mechanisms, such as domain spoofing or email filter evasion, you’re ready to begin sending!
During the sending process, it’s crucial to monitor the campaign’s progress, track email opens, link clicks, credentials harvested, emails responded to, and attachments opened. Depending on the outcome, you may also want to provide additional educational content to victims.
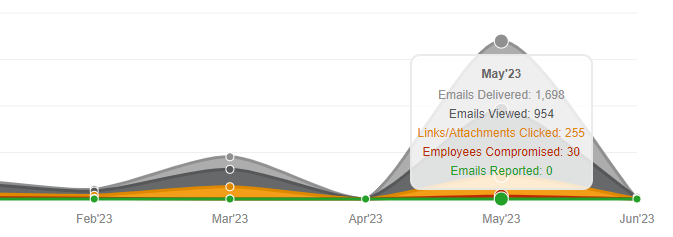
Defending Against Phishing Emails
To better defend against phishing emails, you can implement several different strategies, including:
- Regular Phishing Training: Employees can learn to better detect and report phishing attempts by conducting regular phishing simulations and security awareness training.
- Multi-Factor Authentication (MFA): Implementing MFA makes it more difficult for cybercriminals to gather credentials and access accounts.
- Strong Email Filtering: By deploying advanced email filtering solutions, you can significantly reduce the number of phishing emails that land in employee inboxes. This protection is far from perfect, but it has a significant impact on the likelihood that an employee clicks on a phishing email.
Conclusion
Creating effective and realistic phishing emails is a multi-faceted process that needs to be thoroughly researched to ensure the right email is crafted for the right victim. By following the process outlined in this blog, you’ll be able to significantly increase the phish click rates for your simulated phishing campaigns and ensure you’re replicating real-world threats.
A Security Professional who loves all things related to Cloud and Email Security.





