14 Tips To Become A Hacker In 2026

Becoming a hacker isn't about finding a single exploit or script; it's about developing a mindset that lets you chain small advantages together across different platforms, tools, and environments.
In this blog, we'll guide you on how to become a hacker and share various tools, tactics, and techniques that will help you along the way.
Technical Note:
This guide has been updated to reflect modern tooling, AI-assisted workflows, and evolving attack techniques.It should only be used for legitimate ethical hacking purposes. Ensure you have written permission from individuals or organizations you plan to target with the showcased tools, tactics, and techniques.
1. Access An Environment Where You Can Test Exploits
Having the ability to test exploits is an essential part of learning how to be a hacker. You need to see how exploits are transmitted, how they behave, and what you can do once successfully deployed to truly grasp what it is to have a hacker mindset.
The company 'Offensive Security' has a famous mantra that perfectly idolizes this hacker mindset.
“Try Harder!”
— Offensive Security / From Mantra to Mindset
You have two options when it comes to having access to a hacker-friendly test environment:

Third-Party Cyber Ranges
This is the easier and, in some cases, less expensive approach. The benefit is that cyber ranges are typically shared by dozens or even hundreds of students, meaning the cost of developing and maintaining it is distributed. Companies such as 'Offensive Security' and 'Hack The Box' specialize in providing cyber ranges that are dedicated to helping hackers learn and hone their skill set.

Build Your Own Cyber Range
This is the go-to approach if you need to test exploits or find vulnerabilities in niche or easy-to-setup infrastructure. For example, if you want to test a remote desktop vulnerability that's available in popular versions of Windows, Linux, or macOS operating systems, you could easily spin up a virtual machine on your endpoint or use a cloud computing provider to try this out.
2. Install An Operating System Designed For Hackers
Operating systems like Windows and macOS aren't exactly hacker-friendly. Namely, they don't come preinstalled with hacker tools or their supporting libraries. It's for this exact reason that hackers love to use operating systems like Kali Linux.
The benefit of using an operating system that's purpose-built for hackers is that the maintainers of these operating systems have done a lot of work for you. They've vetted which hacking tools are legitimate and useful, and they categorize them into groups that help you, as the hacker, decide which tools will suit your needs best based on the outcome you're looking for.
To get started with installing an operating system that's designed for hackers, you can simply use virtual machine software, like VirtualBox, to run Kali Linux in a virtual environment on your day-to-day workstation.
3. Familiarize Yourself With Open-Source Hacking Tools
One of the hardest things to do as a hacker is to recognize which tool is going to suit your needs best based on the attack you're performing. Simultaneously, it's crucial to understand which tools give you the biggest return on investment for learning how they work.
Depending on the type of tool, the difficulty of learning how to properly use it can vary significantly. To help you get started, we've collated a list of 5 hacking tools that every hacker should be aware of, regardless of what their specialty is:
- Metasploit: An open-source platform that comes packed with numerous working exploits for a variety of different operating systems, web server technologies, and commercial-off-the-shelf software.
- Nmap: A port and network scanning tool that's indispensable when it comes to network discovery and mapping.
- Wireshark: A network traffic capture tool that lets you intercept and analyze all traffic transiting your device. It's a fantastic tool for discovering vulnerabilities in networked devices.
- Burp Suite: A web application testing tool that lets you send, intercept, and modify web traffic between your desktop and web servers. Burp Suite contains a range of functionalities that help automatically profile and exploit web application vulnerabilities.
- Social-Engineer Toolkit (SET): A tool that's purpose-built for social engineering, particularly phishing. SET can generate phishing content with the click of a button for a variety of popular global services.
Understanding how and why tools fail is just as important as knowing how to use them.
4. Learn How To Program In A Scripting Language
Knowing how to read and write your own scripts is an essential part of being a hacker. You need to be comfortable with reading the scripts that exploits are written in, and be comfortable with modifying them to suit your needs.
Additionally, you'll often need to write small scripts to automate tedious manual tasks. This could be for network discovery, account brute-forcing, web application testing, or any number of things.

5. Study The Lifecycle Of A Cyber Attack
Imagine you want to hack a business and discover all its sensitive secrets. To achieve this goal, you need to understand how to get to those secrets in the first place. This is where understanding the lifecycle of a cyber attack is crucial.
There are a variety of different frameworks that attempt to explain what this lifecycle is (e.g. MITRE ATT&CK Enterprise Matrix and Lockheed Martin Cyber Kill Chain), but we'll simplify it into 5 stages:
-
Reconnaissance
You need to discover everything you possibly can about your target. You're identifying who works for the target, how employees communicate, what their email addresses are if the target has any public-facing infrastructure such as websites, and much more. By utilizing both passive and active reconnaissance techniques, you can identify the best methods for obtaining initial access.
-
Initial Access
You need to get an initial foothold into the target's environment. This could involve compromising a web server, compromising an employee's email account, or compromising an employee's workstation, to name a few.
-
Persistence
Once an initial foothold is obtained, you need to maintain access to that foothold. There's no value in obtaining access if you're immediately kicked out, particularly if you can't achieve your end goal. How initial access was obtained and the level of access you have will dictate how persistence is maintained.
-
Lateral Movement
When persistent access to the target is maintained, you can begin experimenting with tactics that will further your access into the target's environment. Lateral movement could include privilege escalation, laterally moving to other machines on the network, accessing network-accessible resources, and much more. All of this should be done with goal acquisition in mind.
-
Goal Acquisition
Once sufficient access to a target's environment is obtained, it's time to perform your end goal. This could be a variety of things, but typically, for red-team operations, it's a pre-determined flag that's organized between yourself and the customer. By capturing this flag, you can demonstrate that the target was successfully compromised.
6. Develop A Social Engineering Strategy
A common misconception is that social engineering is easy and simple. It's actually a fairly complex process that requires a lot of planning and skills to execute.
Modern social engineering rarely relies on a single channel and often combines email, SMS, voice, and messaging platforms.
In saying this, once you have a strategy in place, social engineering is highly repeatable and effective. You'll want to develop your own social engineering strategy, which is suited to your unique skill set. For example, if you're a good talker, then you'll do well with voice phishing; if you're good with writing, then you'll do well with email phishing, and the list goes on.

Pro Tip: See the CanIPhish blog, which outlines how to become a social engineer.
7. Learn To Create Phishing Content Based On Real Services
Phishing is the most common type of attack both businesses and consumers are facing. In almost all circumstances, your average individual will at least have an email address or phone number that hackers can target for phishing attacks.
To perform a successful phishing attack, you need to know how to create content that replicates trusted and real services that the target individual is familiar with. Depending on the type of phishing attack, you'll need to learn how to create phishing emails or phishing websites for credential harvesting.
This now includes learning to use AI-generated content and synthetic media to increase credibility.
Pro Tip: See the CanIPhish blog, which outlines how to create phishing emails.
8. Learn How To Operate C2 Infrastructure
Regardless of whether your target falls victim to a phishing attack or exploits a vulnerability in a web server, you're going to need command and control infrastructure (also commonly referred to as C2 infrastructure by hackers).
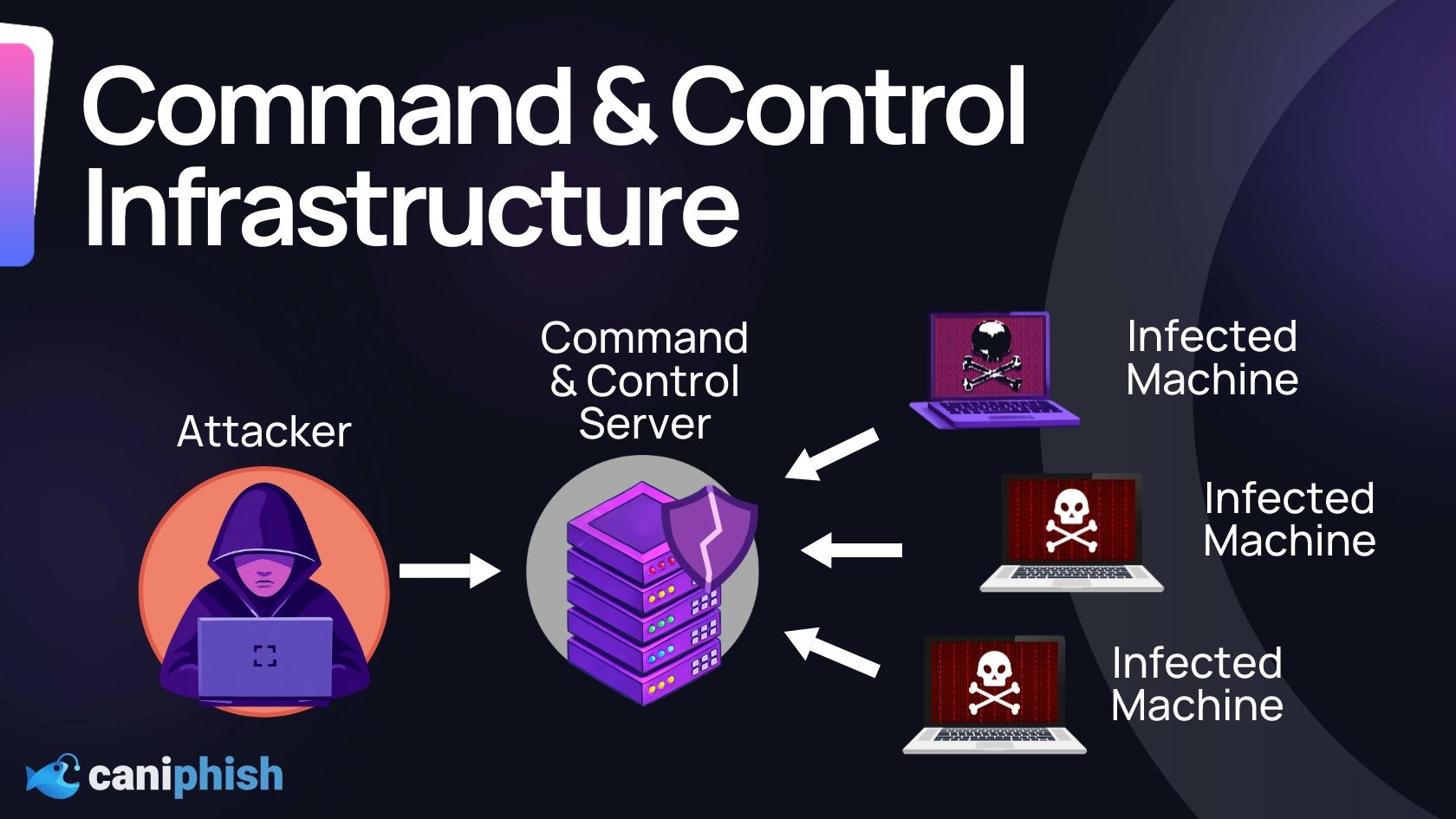
C2 infrastructure is designed to capture and manage access that has been gained to a target environment. Most C2 platforms do this by having the target periodically reach out to C2 infrastructure to open a connection and receive any new commands.
If you're planning to perform any attacks that require persistent access to a target environment, then you'll need to get comfortable with setting up and maintaining C2 infrastructure. In modern environments, noisy or poorly configured C2 infrastructure is often detected quickly by behavior-based monitoring and endpoint detection systems. Fortunately, there are a range of tools that can help with this. The Metasploit Framework, Silver, and Cobalt Strike are popular adversary simulation frameworks providing command and control capabilities.
9. Participate In Capture The Flag (CTF) Competitions
When it comes to hacking, it can be difficult to establish and maintain motivation when there's no defined end goal. CTF competitions help with this by providing both an end goal and motivation by activating the competitive nature that's instilled in most people.
Additionally, CTF competitions are a great way to find like-minded individuals and learn from others. You'll get exposed to tools, tactics, and techniques you wouldn't otherwise encounter. With some luck, you may even get exposed to some N-Day vulnerabilities that hackers keep in their toolkits, should the occasion arise.
10. Follow Hacker News Outlets
By following actively following hacker news outlets, you'll get exposed to the latest tactics and techniques being used in the wild. There are a variety of great news outlets to follow that are available in a number of different mediums, namely:
- NetSec Subreddit: Run by Reddit, r/NetSec is a subreddit where cybersecurity professionals discuss the latest issues related to cybersecurity research, breaches, and emerging threats.
- Darknet Diaries: Hosted by Jack Rhysider, Darknet Diaries is a popular podcast focusing on the underbelly of cybersecurity and hacking, commonly interviewing ex-cybercriminals, state-backed hackers, and cybersecurity professionals.
- Risky Business: Hosted by Patrick Gray, Risky Business (Risky.Biz) is a popular podcast focusing on cyber security and hacking news.
- The Record: Run by Recorded Future, The Record is a popular news outlet focusing on cyber security and hacking news.
- Hacker News: Run by Y Combinator, Hacker News is a popular forum focusing on computer science, hacking, and entrepreneurship.
11. Create Honeypots And Capture Exploits
A honeypot functions by essentially looking like a vulnerable server that entices hackers to attack it. By running a honeypot, you can see exploits thrown at your server and then analyze them in a safe and controlled environment. An important thing to note is that honeypots should never be connected to any sensitive systems.
Honeypots are a great way to uncover details about what types of attacks are increasing in popularity. Numerous threat intelligence and cybersecurity companies run honeypots to help bolster their anti-virus detection systems and add new signatures to the databases they push out to their customer base.
Honeypots are also useful for observing how automated tools and AI-assisted attacks behave in the wild.
12. Define Clear Objectives
This is a practice that every professional hacker should follow.
Before you even think about hacking a target, you need to ask yourself a question. What are my objectives? At the most fundamental level, this can be boiled down to the CIA triad for Confidentiality, Integrity, and Availability. Are you looking to compromise the confidentiality of a system? Are you looking to compromise the integrity of a system? Are you looking to compromise the availability of a system?
By having clearly defined objectives, you can begin to plan what attack will allow you to obtain those objectives. For example, if you want to compromise the availability of a system, you could simply DDoS publicly accessible endpoints. However, if you want to compromise the confidentiality of a system, you need to find a point of entry that provides you with access to view sensitive data - this could involve phishing employees or exploiting system vulnerabilities.
13. Meet Likeminded Individuals
Attending cybersecurity and hacking conferences is a great way to expand your network. You might get job offers, you might make some friends, you might learn about a novel technique for exploiting systems, and if all else fails, you'll at least walk away with some vendor swag.
Depending on where you live, there are likely a number of conferences that you can attend during the year. If you're up for some travel, the most popular conferences worldwide are Black Hat USA and DEF CON.
14. Learn How To Use AI As A Force Multiplier
AI has silently become one of the most powerful tools available to modern hackers. Used correctly, it can accelerate research, learning, and analysis. Used poorly, it can turn you into a copy-paste operator who does not understand what they are doing.
As a hacker, AI should support your thinking, not replace it.
In 2026, hackers use AI to:
- Explain unfamiliar code, exploits, or protocols in simple language
- Help analyze logs, packet captures, or config files
- Generate hypotheses during recon and threat modeling
- Speed up scripting, automation, and documentation
A word of warning: AI can be wrong, incomplete, or misleading. Think of it as a starting point, not the answer.
In 2026, the best hackers will not be the ones who understand its strengths and weaknesses, and know when and when not to use it.

Implementing These Tips
Becoming a hacker may seem challenging, but following these tips will put you in the best position for success. If you're trying to understand how to even get started, then try brainstorming what aspect of hacking interests you most. Is it social engineering? Is it exploiting vulnerabilities in systems, or perhaps it's discovering 0-day vulnerabilities? By answering this question, you'll discover what motivates you, which will ultimately dictate the direction you take from a learning perspective.
Remember, if you run into any roadblocks along the way, follow the OffSec Mantra “Try Harder!”.
Frequently Asked Questions
Is Becoming A Hacker Fun?
Absolutely! The feeling you get when you compromise your first system is next to none. And the great thing? That feeling never stops. You feel great each time you compromise a system or individual, regardless of whether it's part of a penetration test or red-team exercise.
Does Becoming A Hacker Take Long?
Being a hacker is a never-ending learning exercise. There are so many tools, tactics, and techniques that being a hacker is akin to being a professional athlete. You need to keep on top of your skills by continuously practicing, training, and learning new things. If you take a break or stop practicing, your skills diminish over time.
What's The Difference Between A Script Kiddie And A Hacker?
A script kiddie is an individual who runs scripts and tools designed for hackers but doesn't understand the tactics and techniques associated with them. Hackers distinguish themselves by understanding how these scripts and tools fit into the larger cyber attack lifecycle, knowing how to chain multiple tools together, or reaching their end goal, regardless of the specific tool or script in use.
What Are The Most Popular Scripting Languages For Hackers?
The best scripting language is the one you feel most comfortable or knowledgeable with. If you don't have a preferred scripting language, then the most popular ones that hackers use are Python, Perl, PowerShell, and Ruby.
A Security Professional who loves all things related to Cloud and Email Security.