Four Reasons Why Phishing Simulations Contribute To Enterprise Security

- Should Employees Be Able To Spot Social Engineering Attacks?
- How Do Phishing Simulations Contribute To Enterprise Security?
- Reason 1. Security Awareness & Education
- Reason 2. Promoting Cyber Hygiene
- Reason 3. Vulnerability Identification
- Reason 4. Continuous Improvement
- What Should You Look For In A Phishing Platform?
- Wrapping Up
Modern enterprises face an evolving cyber landscape with an endless number of challenges to overcome. We've all seen how cyber security has become a key concern with the ongoing threat of ransomware, cyber extortion, IP theft, and much more.
To address this challenge, many enterprises have begun adopting new cyber security solutions to target attack vectors cyber criminals look to exploit. These include security solutions to protect infrastructure hosted in the cloud, endpoint security solutions to protect employee workstations, and network security solutions to control who can do what and from where.
One attack vector that's overlooked is the cyber readiness of employees. How resilient are they to cyber-attacks, and how likely are they to spot one when it happens?
What You'll Learn In This Article.
- What social engineering is and where phishing fits in.
- What the most popular form of phishing is and why.
- How you can train employees to spot phishing attacks.
- What you should consider when choosing a phishing platform to train employees.
Should Employees Be Able To Spot Social Engineering Attacks?
The short answer is yes. Social engineering is a broad term that encompasses a variety of attacks where the employee is the target. The most popular form of social engineering used to attack enterprises today is phishing, which includes email phishing, SMS phishing, voice phishing, and malicious advertising.
Phishing attacks can have catastrophic consequences for enterprises as the result is typically that the employee is compromised, and anything they have access to may be stolen or made unavailable.
According to the 2022 Data Breach Investigations Report by Verizon, 82% of breaches involved humans falling victim to social attacks, making errors or misusing data and access.

One of the most effective ways to train and protect employees against social engineering attacks is to teach them how to spot phishing attempts. This training typically comes in the form of periodic phishing simulations.
How Do Phishing Simulations Contribute To Enterprise Security?
Put simply, phishing simulations test employees' awareness and response to phishing attacks. These simulations are typically conducted over email but, in some cases, include SMS messages or phone calls.
Training employees through simulated phishing is progressively becoming the go-to method of training employees and new starters. This can be tied back to the fact that phishing is an ever-growing threat for enterprises and that open-source and commercial platforms have made training against this type of attack commercially viable.
Let's deep dive into some of the ways that phishing simulations contribute to enterprise security.
Reason 1. Security Awareness & Education
Employees are educated about the risks of phishing attacks through phishing simulation platforms. Modern phishing simulators include built-in training options designed to provide employees with immediate training should they fall victim to a simulated phish, with optional micro-learning training that can be assigned at a later date.

As phishing simulations are typically conducted periodically, they provide employees with an opportunity to learn from their mistakes. If they fall victim to one phish, they'll learn from the training and become more resilient in future simulations.
Additionally, by educating employees about the risks of phishing, they'll become familiar with the tools, processes, and procedures to follow in the event they fall for an actual phishing attack.
Reason 2. Promoting Cyber Hygiene
Phishing simulations contribute to enterprise security by promoting good security habits and hygiene among employees. By periodically conducting simulations, employees are kept vigilant on the importance of cyber security and how an attacker only needs to be successful once. This practice eventually leads to the development of a security-first mindset and culture among employees.
Employees can also participate in gamification activities by reporting suspected phishing material. A key capability that phishing simulation platforms need to provide is employee risk scoring. By reporting suspected phishing and successfully completing assigned training, employees can decrease their internal risk score, which can also become a key performance indicator tracked by the enterprise.

Reason 3. Vulnerability Identification
Just like how specific applications, software, and operating systems are more prone to vulnerabilities than others, so are employees. Instead of conducting regular or more frequent patching, your most vulnerable employees need to be trained more frequently and have their access permissions evaluated.
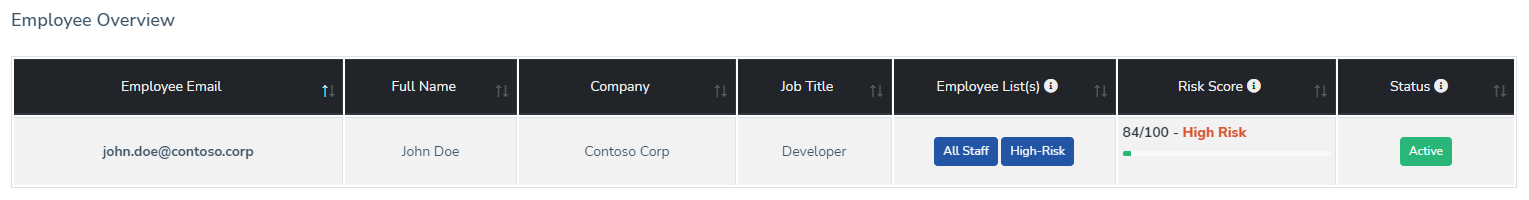
If you have an employee who consistently clicks on phishing material, and that same employee has administrative access to your most trusted assets, perhaps this access should be evaluated until they can prove their cyber resiliency.
Reason 4. Continuous Improvement
The goal of conducting regular phishing simulations is that your employees learn how to spot phishing attempts and lower their phish click rates. At CanIPhish, we've seen enterprises have phish click rates as high as 40%. A good benchmark to aim for with periodic training is phish click rates of 5% or less across the enterprise.
What Should You Look For In A Phishing Platform?
The first step in undertaking a simulated phishing exercise is identifying what you'll use to conduct it.
Cyber criminals invest weeks and even months in researching new techniques to phish employees, and expecting the average business to invest this same amount of time and effort isn't feasible. It's for this reason that the entire vendor ecosystem has been developed, where you can choose from open-source or commercial solutions. Before choosing a solution, you should evaluate which of the following criteria is most important to you:
Competitive Pricing
Open-source tools are available free of charge. However, a commonly overlooked consideration is hosting costs. If you use self-managed open-source tools, you'll be on the hook for hosting the underlying infrastructure and maintaining it. This alone often deters enterprises away from the open-source route and more towards commercial solutions that offer managed mail and web infrastructure.
Mature Capabilities
Phishing simulation solutions should always provide a realistic phishing experience. This includes delivering phishing emails, hosting phishing websites, supporting the delivery of attachments, tracking email responses, and even allowing for the use of email domain spoofing.
Micro-Learning Training
Phishing simulations should be combined with security awareness training. This training can include immediate guidance in the event an employee falls victim to a simulated phish and ad-hoc periodic training assignments, which can be delivered as micro-training modules.
Strong Roadmap
Phishing threats are constantly evolving, and any solution chosen should have a near and long-term roadmap that customers can use to understand what is being done to ensure the latest phishing trends are being accounted for.
Wrapping up
Phishing simulations are an effective way for enterprises to bolster their cyber security posture and should be used as part of a layered defense-in-depth approach. Simulated phishing attacks, promote good cyber hygiene, identify vulnerable employees, and provide an opportunity for continuous improvement.

If you're interested in evaluating a phishing simulation and security awareness training platform, try the free Cloud Platform offered by CanIPhish. You can sign-up in seconds and send your first phish in minutes. If you have any questions, please don't hesitate to contact us.
Sebastian Salla
A Security Professional who loves all things related to Cloud and Email Security.