The 10 Most Damaging Hacks In History

Looking to uncover the most damaging hacks in history?
In this blog, we're counting down 10 real-life hacks that shook governments, paralyzed businesses, and exposed millions of people, with each hack leaving a mark on cybersecurity history. Let's dive in.
10. Sony PlayStation Network Breach (2011)

Imagine losing access to your favorite game for 23 days straight.
That's precisely what happened in April 2011, when Sony had to pull the plug on the entire PlayStation Network when it discovered a breach.
The global shutdown wasn't optional. It was damage control. Users lost access to games, movies, and online services. For almost a month, millions of users were cut off from their digital world.
Hackers gained access to the personal data of 77 million users, making it one of the most high-profile data breaches in gaming history.
Stolen information included names, email addresses, home addresses, usernames, passwords, birthdates, and possibly even encrypted credit card details.
Sony reported an estimated $171 million USD in direct costs, covering customer support, compensation, and major security upgrades.
When you add fines, lawsuits, and the long-term hit to brand trust, the real damage likely runs much higher.
It was one of the priciest wake-up calls in gaming history, exposing just how vulnerable even the biggest platforms can be.
9. Target Data Breach (2013)

In late 2013, during their busiest shopping season of the year, Target lived up to its name. Literally, the retail giant became a victim of one of the most significant and damaging retail cyberattacks in history.
The air conditioner guy was the weak link that made it all possible. Cybercriminals gained access to Target's internal network via an HVAC vendor. That access existed so they could remotely monitor and manage heating, ventilation, and air conditioning systems. It enabled real-time tracking of HVAC operations, including temperature settings, energy usage, and maintenance alerts. Unfortunately, that pathway opened the door to the attackers, and they walked right in.
From there, they quietly moved through the network until they hit the point-of-sale (POS) systems, where customer credit card data lived. There, they deployed BlackPos, a memory-scraping malware that captured credit card details before they were sent for payment processing. The malware cleverly operated during business hours to avoid detection.
Over 3 weeks, the attackers captured 40 million payment card records and the personal information of another 70 million customers. This included names, addresses, phone numbers, and emails.
The worst part was that this attack did actually trigger alarm bells. Target's security system picked up the breach in real time, but the warning signs were ignored or dismissed. That's like your home alarm system going off and someone saying, "Eh, it's probably just the wind."
Target faced roughly $250 million USD in total losses, including lawsuits, settlements, and a massive security overhaul. The CIO and CEO both stood down, and the company spent years rebuilding customer trust and tightening vendor access.
8. Yahoo Breaches (2013–2014)

This wasn't just your standard breach. It was the breach.
Yahoo is now known for the largest data breach in history, with 3 billion user accounts compromised in a single breach.
Three billion. With a B.
And that's not even the worst part. It happened twice.
Between 2013 and 2014, Yahoo suffered two separate breaches that compromised nearly every user account. You name it: emails, phone numbers, birthdates, names, even security questions.
To make matters worse, the public found out years later!
The first breach occurred in August 2013. It is believed to have been executed by state-sponsored hackers and affected 3 billion user accounts.
Then, in late 1014, it happened again. An individual group reportedly carried out this one. The group used forged cookies to gain access to users' accounts without needing passwords.
In 2016, Yahoo was forced to disclose the extent of the breach, right in the middle of a $4.8 billion acquisition deal with Verizon. That disclosure was not only embarrassing, but it also caused Verizon to slash $350 million off the asking price.
Yahoo's financial fallout is estimated to be around $600 million USD.
Fair enough if this was some cutting-edge, zero-day exploit, but it wasn't. This all happened due to bad security practices, outdated encryption, reused credentials, and years of neglect.
In the end, it wasn't elite hackers that brought Yahoo down. It was their own security shortcuts that did it.
7. Poly Network Exploit (2021)

Only in Crypto can you steal $600 million and walk away with a job offer.
In 2021, Poly Network, a platform that allows users to move cryptocurrency across blockchains, was hit hard by a massive exploit.
The attacker found a vulnerability in the Poly Network's smart contract code and tricked it into thinking they had permission to move funds. Within 24 hours, they had drained roughly $610 million USD in crypto assets across Ethereum, Binance Smart Chain (BSC), and Polygon, the three biggest blockchain networks connected to the platform.
The breach affected thousands of users. Poly Network posted an open letter pleading with the hacker to return the funds. Since every transaction on the blockchain is traceable, the attacker couldn't cash out without risking exposure of their identity.
Instead of disappearing, the hacker started talking directly with Poly, who nicknamed them "Mr. White Hat."
Over the next 15 days, most of the stolen assets were returned, claiming that it was done "for fun" and to expose vulnerabilities before others could.
Poly Network thanked them, offered a $500,000 bug bounty, and even extended a job offer as Chief Security Advisor.
Both offers were declined, but reports suggest the funds were still sent to the hacker's wallet. It's unclear whether they ever used or returned the bounty, but on record, it was declined.
In the end, no arrests were made, and no charges were filed. The attacker walked away with a job offer, a generous thank-you gesture, and a credit for pulling off the largest "ethical" theft in crypto history.
6. Marriott / Starwood Breach (2018)

When Marriott acquired Starwood Hotels in 2016, it was supposed to be a business win, not a cybersecurity nightmare.
Instead of extra revenue, they inherited a network that had been compromised since 2014.
The cybercriminals used a Remote Access Trojan (RAT) to get in, then used a tool called Mimikatz to upgrade their permissions and laterally move around the Marriott network.
Over a two-year period, hackers quietly collected guests' names, email addresses, phone numbers, birthdates, genders, mailing addresses, and even arrival and departure details. Card details were also swept up. The information was apparently encrypted, but Marriott couldn't confidently say that the hackers didn't get both halves of the decryption key.
They later confirmed that 5.25 million unencrypted passport numbers were exposed, and millions more were only partially protected.
That's five stars for stealth.
Around 383 million guest records had been compromised, making it one of the biggest data breaches in the hospitality industry.
The damage from the Marriott breach is estimated to exceed $500 million USD, once you tally up legal payouts, fines, response costs, and the long-term brand damage that makes many people think twice about booking a room there.
5. Stuxnet (2010)

Most worms go for red tomatoes. This one went for centrifuges.
Stuxnet was a sophisticated computer worm, malicious software that spreads and executes independently. But this one was different from a typical worm. Most malware is built to steal data, spy on users, and demand a ransom. It was designed to sabotage Iran's industrial control systems, specifically SCADA networks running the centrifuges at Natanz.
Widely believed to be created by the US and Israeli governments, Stuxnet spread via infected USB drives, requiring no internet to propagate.
The worm secretly altered the speed of the uranium centrifuges, spinning out of control and self-destructing while making everything appear normal to the systems operator. The damage to the centrifuges set Iran's nuclear efforts back by years.
The total financial damage caused by Stuxnet is speculated to be between $1 and $2 billion USD, accounting for the damage, delays, and cleanup costs.
It was the first malware to cause physical destruction, setting a new milestone in the history of cyberwarfare.
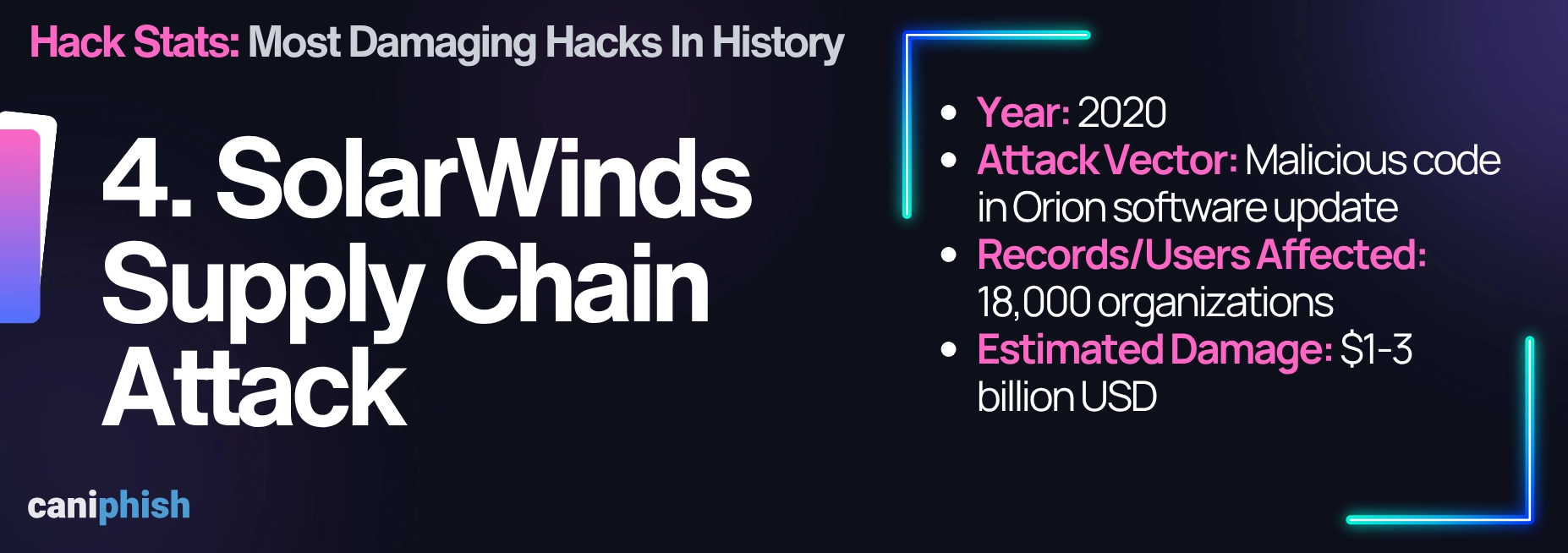
4. SolarWinds Supply Chain Attack (2020)
What could possibly go wrong with a routine software update?
For SolarWinds, it was just a full-blown international cyber-espionage disaster. No biggie.
In 2020, hackers managed to pull off one of the most devastating supply chain attacks in history.
SolarWinds is a software company that provides a popular software platform called Orion that is used by thousands of companies globally for system monitoring.
The hackers, believed to be state-sponsored Russian hackers, slipped malicious code into a legitimate Orion update. The update was then downloaded by around 18,000 unsuspecting customers. This included some high-profile organizations like the US Treasury, Department of Homeland Security, Microsoft, Cisco, and FireEye.
Once installed, it stayed quiet in the network for months. The malware gave the attackers remote access to the internal systems, emails, and sensitive data.
The financial impact is estimated to be between $1 and $3 billion USD. Why the range? The actual cost is still unfolding. Between the regulatory fines, lawsuits, breach investigations, insurance payouts, and customer fallouts, it's a slow-motion avalanche. Just one insurance firm pegged insured losses at $90 million alone.
So next time your IT guy tells you to "just run the update," maybe double-check it isn't secretly backdoored by a foreign intelligence agency.
3. Equifax Breach (2017)

Equifax had the option to fix a critical vulnerability but chose to hit snooze, leading to meme-worthy disgrace.
In 2017, Equifax, one of the big three credit reporting agencies, suffered a massive breach that exposed the sensitive personal data of 147 million Americans. Nearly half the US population!
The hackers walked away with basically everything to ruin your life. Names, Social Security numbers, birthdates, home addresses, even some driver's license numbers and credit card details.
Equifax was using a web application built on Apache Struts. The attackers exploited a known vulnerability, one that already had a patch available for 2 months. Unfortunately, Equifax hadn't applied it, letting cybercriminals walk right in.
It took Equifax 6 weeks to disclose the breach, and their response wasn't exactly professional. Instead of using their official site to share breach info, they launched a separate domain. The domain was accidentally linked to phishing sites on social media. They also messed up the PINs that were meant to protect the consumer credit freezes. Doh! Talk about a mess.
The fallout was massive. Depending on the estimate, the breach cost Equifax between $1.4 and $4 billion USD in fines, settlements, cleanup, and remediation.
No amount of money in fines can undo the damage done. Unlike a credit card, you can't just request a new Social Security number and expect one to show up in the mail five to seven business days later.
2. WannaCry Ransomware (2017)

Imagine being booked in for life-saving surgery, only to have it canceled due to a ransomware worm.
That's what happened in May 2017. A ransomware worm called WannaCry didn't just spread, it sprinted across the world.
It locked up over 200,000 systems in more than 150 countries, causing global chaos in record time.
This crippled hospitals, businesses, logistic companies, telecoms, governments, and anything else running outdated Windows systems. The UK's National Health Service was hit so hard that it was forced to cancel surgeries and appointments. In Spain, Telefónica told staff to "just turn your computer off."
WannaCry exploited a Windows flaw called EternalBlue, a hacking tool built by the NSA and later leaked by a group called Shadow Brokers.
WannaCry would encrypt files, then hold them hostage for $300 in Bitcoin. Wait too long, and the price doubles. Still didn't pay? Files gone.
Payment didn't guarantee anything. It didn't have a reliable payment or decryption system. Some victims paid and still got nothing. Classic ransomware customer service.
Total damages are estimated at $4-8 billion USD, and that's just the financial side of things. The reputational blow to organizations was priceless.
North Korea's Lazarus Group, a state-sponsored hacking crew, is widely believed to be responsible for WannaCry. While North Korea denies it, cybersecurity firms have traced it back to them.
1. NotPetya Malware (2017)

Coming in as the most damaging hack of all time... NotPetya.
2017 was not a good year in the digital world!
First came WannaCry, then, just as the dust was settling. Boom. NotPetya showed but wasn't here to play fair. It wasn't about money, it was about destruction.
The attack began in June 2017 and affected businesses, banks, airports, and government agencies, mostly in Ukraine. But like most cyberattacks, it didn't stay local for long. It went global fast.
The malware spread via a compromised software update from M.E.doc, a widely used Ukrainian accounting tool. Thousands of businesses unknowingly stalled the infected update, giving the attackers direct access to their internal networks. Some were hit so hard, they had to build entire networks from scratch.
Once inside, NotPetya used EternalBlue (the same NSA-built exploit from WannaCry), Mimikatz, and brute-force credential theft to move laterally through networks like wildfire.
Unlike WannaCry, which was all about the money, NotPetya was not interested in the payouts. It was built to destroy. Even if you did pay the ransom, your files were gone for good. There was no recovery, no reversal. Just chaos.
The attack was allegedly carried out by a state-sponsored Russian hacking group linked to the GRU, though no official attribution has been universally confirmed.
The NotPetya attack easily caused over $10 billion USD in global damage. Major companies like Maersk, FedEx, Merck, and others were forced to shut down operations, rebuild, and face multi-million dollar setbacks.
Entire organizations ruined. But hey, at least no one made any money.
Wrapping up
So there you have it!
From billion-dollar breaches to ransomware worm wipeouts, these weren't just hacks, they were full-blown cybersecurity wake-up calls.
Each reminds us of how fragile the digital world can be and how priceless solid security practices can be.
Some had state-sponsored digital muscle behind them, while others were driven by cybercriminals chasing easy money. All of them left a trail of chaos.
If there's one thing security teams should've learned from all this, it's this; if there's a patch available, apply it. ASAP.
Otherwise, your organization might make headlines for all the wrong reasons.
Step Into The Mind Of A Hacker
The Social Engineer is a high-stakes, turn-based cyber game where you play as an up-and-coming criminal mastermind.
Play now!An Operations Analyst on a mission to make the internet safer by helping people stay a step ahead of cyber threats.
